Search for "283" returned 2296 results
63 min
Exploiting Symbian
Symbian Exploit and Shellcode Development

53 min
Towards a Single Secure European Cyberspace?
What the European Union wants. What the hackerdom can do..
64 min
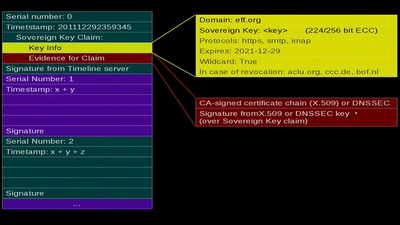
Sovereign Keys
A proposal for fixing attacks on CAs and DNSSEC
66 min
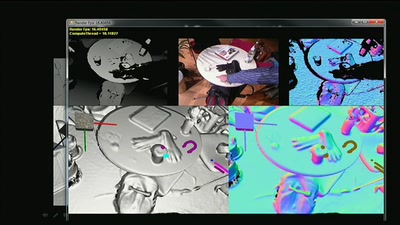
KinectFusion
Real-time 3D Reconstruction and Interaction Using a Moving…

51 min
Apple vs. Google Client Platforms
How you end up being the Victim.
60 min
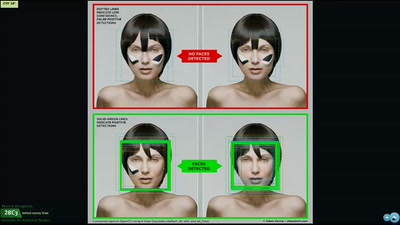
Macro dragnets: Why trawl the river when you can do the whole ocean
What happens when data collection goes awry in the 21st…

43 min
CCC Jahresrückblick
Ein Überblick über die Aktivitäten des Clubs 2005

45 min
Privacy in the social semantic web
Social networks based on XMPP

25 min
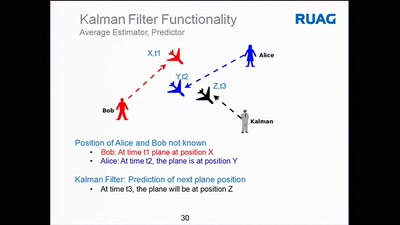
Security Log Visualization with a Correlation Engine
What's inside your network?
54 min
Datamining for Hackers
Encrypted Traffic Mining

64 min
„Die Koalition setzt sich aber aktiv und ernsthaft dafür ein“
Sprachlicher Nebel in der Politik

65 min
Quantified-Self and OpenBCI Neurofeedback Mind-Hacking
Transhumanism, Self-Optimization and Neurofeedback for…

67 min
Datenvieh oder Daten-Fee
Welchen Wert haben Trackingdaten?
51 min
SCADA and PLC Vulnerabilities in Correctional Facilities
Tiffany Rad, Teague Newman, John Strauchs

51 min
Algorithmic Music in a Box
Doing music with microcontrollers
60 min
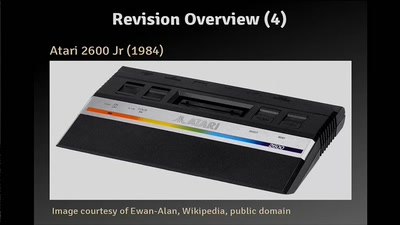
The Atari 2600 Video Computer System: The Ultimate Talk
The history, the hardware and how to write programs

62 min