Search for "andi" returned 7404 results
55 min
The Computer Science behind a modern distributed data store
The science it takes to build a multi-threaded, clustered…

62 min
Corporate surveillance, digital tracking, big data & privacy
How thousands of companies are profiling, categorizing,…
34 min
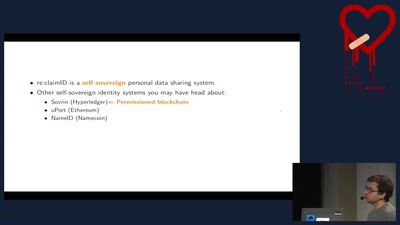
re:claimID
A GNUnet Application for Self-sovereign, Decentralised…

63 min
A look into the Mobile Messaging Black Box
A gentle introduction to mobile messaging and subsequent…

48 min
DRM comes to European digital TV
How the DVB project is locking down TV standards and…

59 min
Understanding buffer overflow exploitation
The fascinating interplay of CPU, stack, C-compiler and…
40 min
Art against Facebook
Graffiti in the ruins of the feed and the…

63 min
The Case Against WikiLeaks: a direct threat to our community
How to understand this historic challenge and what we can…
42 min
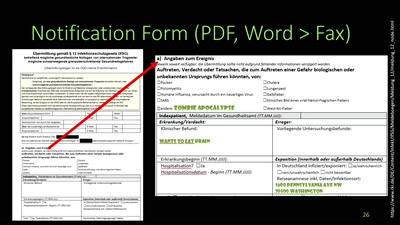
Zombie Apocalypse vs. International Health Regulations
Introducing a very important piece of international law and…
60 min
IoT ethics
what I found out using my home and body as a test lab
64 min
Are Whistleblowers safer today than they were at OHM2013?
Current case studies of whistleblowing in Europe, and how…

70 min
coreboot: Adding support for a system near you
Working with the open source BIOS replacement and getting a…

55 min
Independents unite! Inside the freelancers’ movement
How to learn from online communities and coworking spaces…
56 min
The importance of resisting Excessive Government Surveillance
Join me in exposing and challenging the constant violations…
38 min
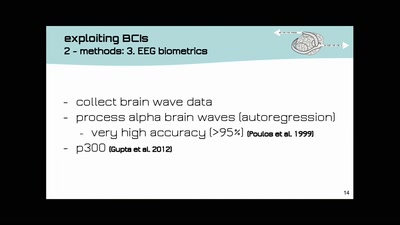
Open-BCI DIY-Neuroscience Maker-Art Mind-Hacking
open source DIY brain-computer-interfaces | technology and…

52 min
Funkerspuk
radio politics in the USA and Germany in the first half of…

57 min
The Precariat: A Disruptive Class for Disruptive Times.
Why and How the Precariat will define the Global…
63 min
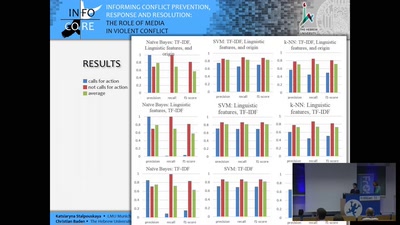
Pushing the frontiers of Information Extraction:
A Strategy for for Identifying Calls for Action in Texts…
65 min
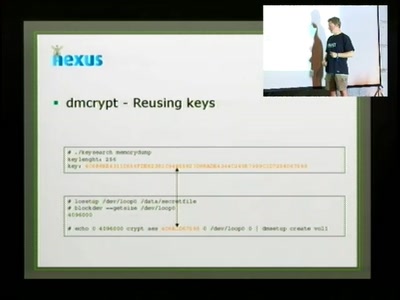
Cryptographic key recovery from Linux memory dumps
Does dm-crypt and cryptoloop provide expected security when…
52 min
A 10GE monitoring system
Hacking a 10 Gigabit Intrusion detection and prevention…

56 min
Rootkits in your Web application
Achieving a permanent stealthy compromise of user accounts…

58 min