Search for "264" returned 2200 results
56 min
Making Technology Inclusive Through Papercraft and Sound
Introducing the Love to Code Platform

59 min
Security of the IC Backside
The future of IC analysis
61 min
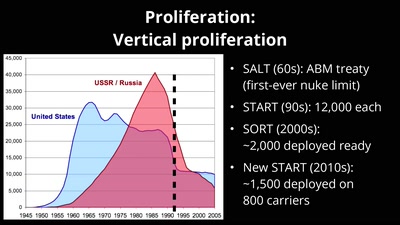
What Ever Happened to Nuclear Weapons?
Politics and Physics of a Problem That's Not Going Away

60 min
Quantum Cryptography
from key distribution to position-based cryptography

59 min
Fernvale: An Open Hardware and Software Platform, Based on the (nominally) Closed-Source…
A Lawful Method for Converting Closed IP into Open IP

60 min
The Exploration and Exploitation of an SD Memory Card
by xobs & bunnie
63 min
This Is Not A Game
Eine kurze Geschichte von Q als Mindfuck-Spiel

55 min
Fuzzing the phone in the iPhone
D-d-d-di-di-d-d-di-d-di-d-di-d-dimm!

43 min
Microtargeting und Manipulation
Von Cambridge Analytica zur EU-Wahl
41 min
Archäologische Studien im Datenmüll
Welche Daten speichert Amazon über uns?

46 min
Practical Mix Network Design
Strong metadata protection for asynchronous messaging

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…

33 min
Rebel Cities
Towards A Global Network Of Neighbourhoods And Cities…

30 min