Search for "Victor van der Veen" returned 181 results

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data

57 min
TrustZone-M(eh): Breaking ARMv8-M's security
Hardware attacks on the latest generation of ARM Cortex-M…
58 min
Script Your Car!
Using existing hardware platforms to integrate python into…

58 min
Glitching For n00bs
A Journey to Coax Out Chips' Inner Secrets

31 min
JODI - Apache is functioning normally
A net.art collective since 1995. Understanding the browser…

41 min
Breathing Life into Legacy: An Open-Source Emulator of Legacy Apple Devices
A Dive into Reverse Engineering and Understanding the iPod…

60 min
Concepts for global TSCM
getting out of surveillance state mode

42 min
NEW IMPORTANT INSTRUCTIONS
Real-world exploits and mitigations in Large Language Model…

60 min
APT Reports and OPSEC Evolution, or: These are not the APT reports you are looking for
How advanced threat actors learn and change with innovation…

59 min
We should share our secrets
Shamir secret sharing: How it works and how to implement it
38 min
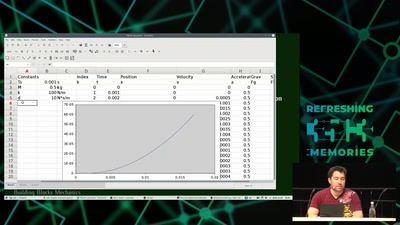
Modeling and Simulation of Physical Systems for Hobbyists
Essential Tools for Developing, Testing and Debugging…

63 min
goto fail;
exploring two decades of transport layer insecurity

60 min
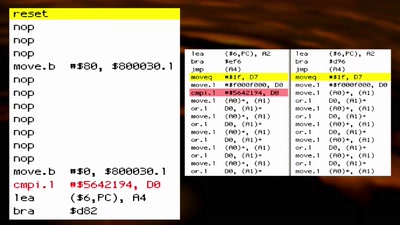
osmo-gmr: What's up with sat-phones ?
Piecing together the missing bits
38 min
Unpacking the compromises of Aadhaar, and other digital identities inspired by it
Governments around the world are implementing digital…
61 min
Rocket Kitten: Advanced Off-the-Shelf Targeted Attacks Against Nation States
A Deep Technical Analysis
26 min
Plants & Machines
Food replicating Robots from Open Source Technologies

46 min
Taking a scalpel to QNX
Analyzing & Breaking Exploit Mitigations and Secure Random…

58 min