Search for "322" returned 2123 results

60 min
Beyond Anti Evil Maid
Making it easier to avoid low-level compromise, and why…

58 min
When hardware must „just work“
An inside look at x86 CPU design

60 min
Concepts for global TSCM
getting out of surveillance state mode

57 min
How I Learned to Stop Reinventing and Love the Wheels
or having FUN with (home/hackerspace) robotics

58 min
Baseband Exploitation in 2013
Hexagon challenges

55 min
White-Box Cryptography
Survey

58 min
Paypals War on Terror
A Historical Re-Enactment of the PayPal14

46 min
Electronic Evicence in Criminal Matters
An introduction and critique of the EC proposal for a…

51 min
Virtual Secure Boot
Secure Boot support in qemu, kvm and ovmf.

63 min
A look into the Mobile Messaging Black Box
A gentle introduction to mobile messaging and subsequent…

49 min
Dissecting VoLTE
Exploiting Free Data Channels and Security Problems

41 min
Extracting keys from FPGAs, OTP Tokens and Door Locks
Side-Channel (and other) Attacks in Practice

58 min
Switches Get Stitches
Industrial System Ownership
59 min
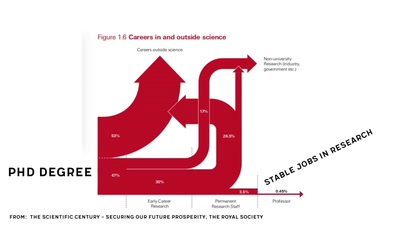
Scientific Literacy 101
Let's understand how the scientific system works

64 min