Search for "console" returned 167 results
49 min
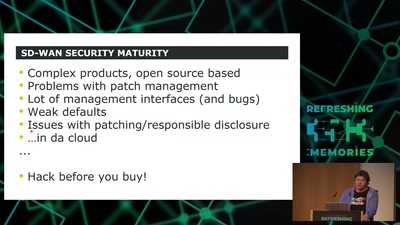
SD-WAN a New Hop
How to hack software defined network and keep your sanity?
60 min
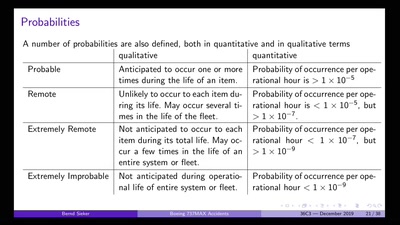
Boeing 737MAX: Automated Crashes
Underestimating the dangers of designing a protection system

57 min
Everything you want to know about x86 microcode, but might have been afraid to ask
An introduction into reverse-engineering x86 microcode and…

49 min
BREACH in Agda
Security notions, proofs and attacks using dependently…
43 min
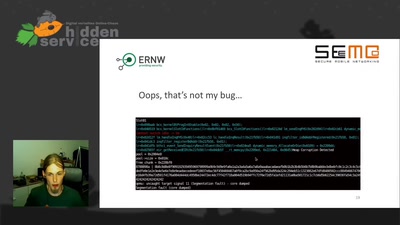
No PoC? No Fix! - A sad Story about Bluetooth Security
It is just a broken memcpy in the Bluetooth stack. Do we…
38 min
KOALitionsvertragsAnalyse
Mit Tools & Methoden dem Vertrag auf den Zahn fühlen

63 min
Dissecting HDMI
Developing open, FPGA-based capture hardware for conference…
58 min
Confessions of a future terrorist
A rough guide to over-regulating free speech with…
40 min
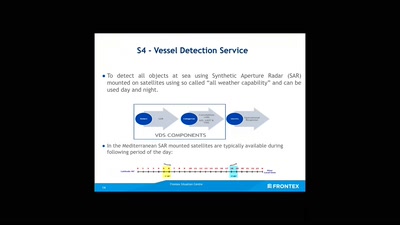
No roborders, no nation, or: smile for a European surveillance propagation
How an agency implements Fortress Europe by degrading…
55 min
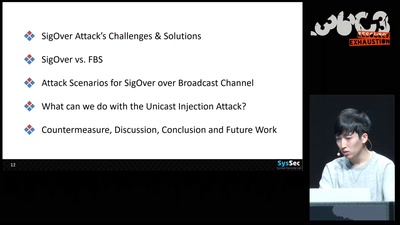
SigOver + alpha
Signal overshadowing attack on LTE and its applications

44 min
Disclosure DOs, Disclosure DON'Ts
Pragmatic Advice for Security Researchers

54 min
How (not) to build autonomous robots
Fables from building a startup in Silicon Valley

51 min
Funky File Formats
Advanced binary tricks

54 min
Attacking Chrome IPC
Reliably finding bugs to escape the Chrome sandbox

31 min
The Clash of Digitalizations
The Devolution of Arab Men from Humans to Digital Fodder

59 min
Security of the IC Backside
The future of IC analysis

60 min
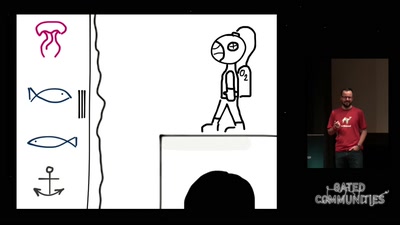
The Exploration and Exploitation of an SD Memory Card
by xobs & bunnie
59 min
Top X* usability obstacles
*(will be specified later based on usability test with…

57 min