Search for "ICAN"
prev
next
51 min
What goes into playing defence and what can be holding you…

60 min
How citizens can hack the legislative process to protect…
43 min
How Curiosity's Onboard Computer works, and what you can…

33 min
How can we make sure that young people's voices are heard…

52 min
Eine Lesung aus dem Buch "Schwarzbuch Datenschutz"

69 min
Encrypting (GSM) mobile phone calls over VPN with an…

56 min
Neue Entwicklungen beim ePass

62 min
Hot or Not: Defeating anonymity by monitoring clock skew to…

138 min
The story of the dutch campaign against black-box voting to…
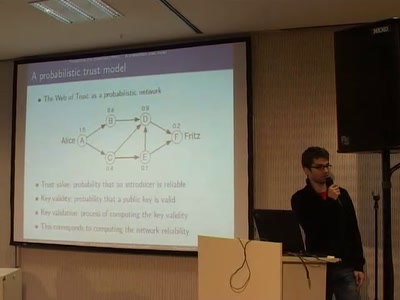
55 min
A new way of evaluating a PGP web of trust by using a…

53 min
How to find, invade and kill botnets automated and…
50 min
Autonomous flying vehicles

34 min
XMPP ist viel mehr als nur Instant Messaging

54 min
Take a lot of Perl, add some OpenSSL, sprinkle it with a…
30 min
It is time to check if we can use a mobile device with a…

33 min
What can be done to protect the term, the notion and the…
60 min
How private companies leak your personal data into the…

63 min
Is your data secure by default? How Django can be used to…

63 min
Mandatory Access Control und TPM in Xen
prev
next












