Search for "Mitch" returned 1175 results

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…

30 min
Information Control and Strategic Violence
How governments use censorship and surveillance as part of…

30 min
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches

48 min
Don't Ruck Us Too Hard - Owning Ruckus AP Devices
3 different RCE vulnerabilities on Ruckus Wireless access…
32 min
Coding your body
How to decipher the messages of your body

61 min
Uncaging Microchips
Techniques for Chip Preparation

40 min
Das Mauern muss weg
Best of Informationsfreiheit
39 min
The Eye on the Nile
Egypt's Civil Society Under Attack
31 min
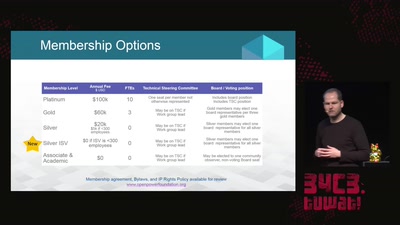
openPower - the current state of commercial openness in CPU development
is there no such thing as open hardware?
59 min
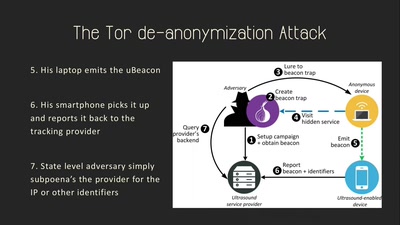
Talking Behind Your Back
On the Privacy & Security of the Ultrasound Tracking…

56 min
Reality Check! Basel/Lagos?? In virtual reality?
An African tale of art, culture and technology

40 min
An introduction to Firmware Analysis
Techniques - Tools - Tricks

39 min
Venenerkennung hacken
Vom Fall der letzten Bastion biometrischer Systeme
58 min
Confessions of a future terrorist
A rough guide to over-regulating free speech with…
59 min
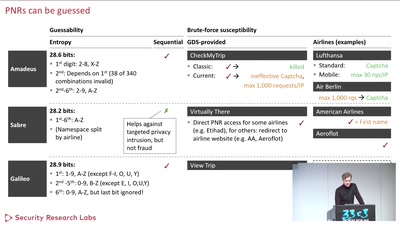
Where in the World Is Carmen Sandiego?
Becoming a secret travel agent
46 min
Maker Spaces in Favelas - Lecture
Engaging social innovation and social innovators

60 min
What does Big Brother see, while he is watching?
Uncovering images from the secret Stasi archives.
56 min