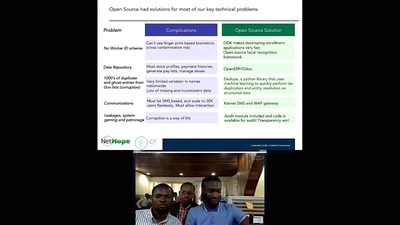
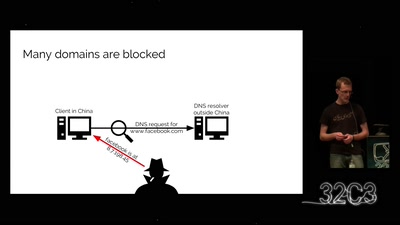
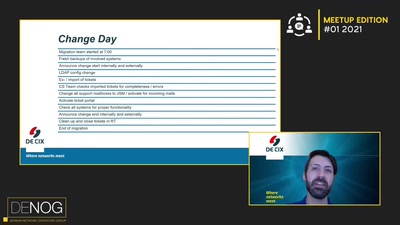
Search for "694" returned 1886 results

61 min
CAESAR and NORX
Developing the Future of Authenticated Encryption

60 min
Crypto Wars Part II
The Empires Strike Back

42 min
A world without blockchain
How (inter)national money transfers works

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

48 min
REXUS/BEXUS - Rocket and Balloon Experiments for University Students
How to bring student experiments into space.
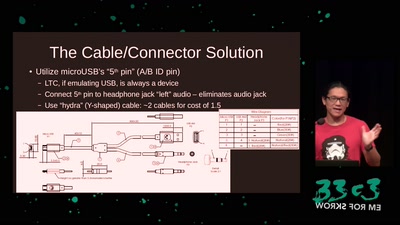
56 min
Making Technology Inclusive Through Papercraft and Sound
Introducing the Love to Code Platform

59 min
Security of the IC Backside
The future of IC analysis
61 min
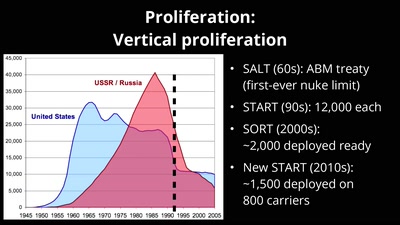
What Ever Happened to Nuclear Weapons?
Politics and Physics of a Problem That's Not Going Away

60 min
Quantum Cryptography
from key distribution to position-based cryptography

59 min
Fernvale: An Open Hardware and Software Platform, Based on the (nominally) Closed-Source…
A Lawful Method for Converting Closed IP into Open IP

60 min
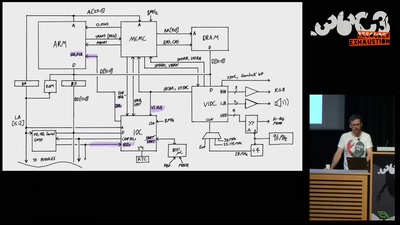
The Exploration and Exploitation of an SD Memory Card
by xobs & bunnie
43 min
No PoC? No Fix! - A sad Story about Bluetooth Security
It is just a broken memcpy in the Bluetooth stack. Do we…

60 min
What does Big Brother see, while he is watching?
Uncovering images from the secret Stasi archives.

29 min
The Pirate Cinema
Creating mash-up movies by hidden activity and geography of…

41 min
MicroPython – Python for Microcontrollers
How high-level scripting languages make your hardware…

43 min
Speaking Fiction To Power
Strategies and tactics to ‘hack’ public spaces and social…
58 min