Search for "【"m" returned 11767 results

30 min
The quest for artificial general intelligence
beyond the Turing test
52 min
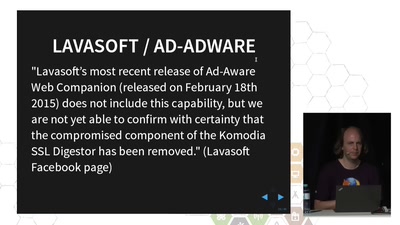
TLS interception considered harmful
How Man-in-the-Middle filtering solutions harm the security…
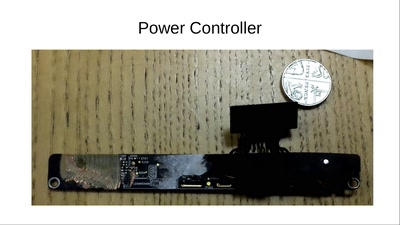
58 min
How to Destroy a Laptop with Top Secrets
How did GCHQ do it to the Guardian's copy of Snowden's…

45 min
Fueling the Revolution
Personal production of bio-fuels
56 min
Helping the Helpless
Targeted threats to civil society

27 min
Experimental Fermentation Institutes Network (EFIN)
fermenting together for better future
28 min
Hardware attacks: hacking chips on the (very) cheap
How to retrieve secret keys without going bankrupt
60 min
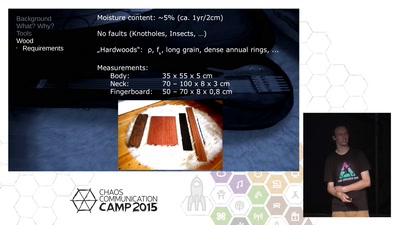
A Hackers Approach To Building Electric Guitars
Let's do everything except the pots by ourselves
![for women in "${tech[@]}"; do](https://static.media.ccc.de/media/conferences/camp2015/6774-hd.jpg)
26 min
for women in "${tech[@]}"; do
Let's talk, share and learn from each other.

28 min
Gotta Block’em all
Creating a usable tool against online trackers

26 min
Data and discrimination: representing marginalised communities in data
The right to be counted, or the right to be left alone?

27 min
Analogue Mission Simulations
Wait what? Why not digital?
69 min
The hills are alive with the sound of hacking ... don't wake the monkeys!
The State of the Hack in India. A place to be^W hack in the…

54 min
Staatstrojaner in Karlsruhe
Anhörung zur verdeckten Infiltration von IT-Systemen
46 min
Bugged Files
Is Your Document Telling on You?

30 min
A Torifying Tale
Our experiences of building and running Tor servers

21 min
Goethe in my Mind
Computer haben Gefühle, wir helfen ihnen, sie auszudrücken
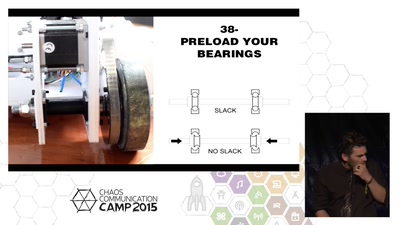
30 min
A practical prototyping primer
A rather unstructured selection of things I wished I knew…

36 min
Mier – failure attempt to CC license as mass market consume good
A creative drink for the commons

34 min
Digital Musical Instruments
Evolution and design of new interfaces for musical…

24 min
Building your First Combat Robot
Nothing shows pride like letting others destroy what you’ve…

40 min