Search for ".rif" returned 2137 results
38 min
Unpacking the compromises of Aadhaar, and other digital identities inspired by it
Governments around the world are implementing digital…

46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database

60 min
Attacking end-to-end email encryption
Efail, other attacks and lessons learned.
39 min
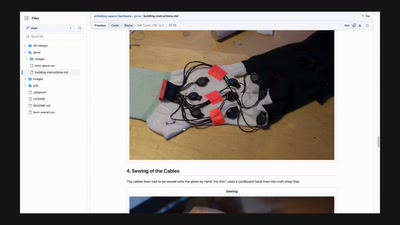
The Unfolding Space Glove
A Wearable for the Visually Impaired Translating 3D Vision…
27 min
Cyborg Foundation
Transpecies Society

40 min
Domain computers have accounts, too!
Owning machines through relaying and delegation
65 min
LatticeHacks
Fun with lattices in cryptography and cryptanalysis
32 min
"Stimme in Konzerne hacken"
Herausforderungen & Lösungen um das Medium Podcast in…
39 min
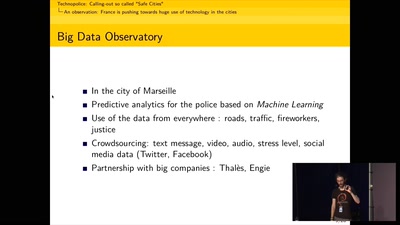
Technopolice: calling out so-called "Safe Cities"
Decentralising the fight against automated surveillance in…

36 min
Apple's iPhone 15: Under the C
Hardware hacking tooling for the new iPhone generation

63 min
The Case Against WikiLeaks: a direct threat to our community
How to understand this historic challenge and what we can…
41 min