Search for "林水成董事長股份tVwo" returned 1557 results
31 min
Growing Up Software Development
From Hacker Culture to the Software of the Future

46 min
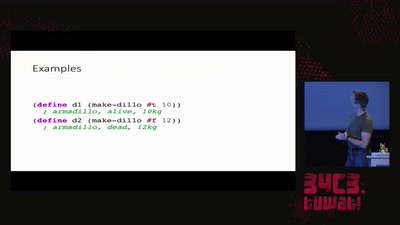
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database
52 min
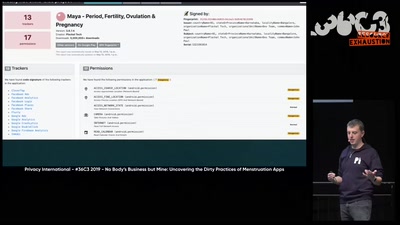
No Body's Business But Mine, a dive into Menstruation Apps
The Not-So Secret Data Sharing Practices Of Menstruation…
65 min
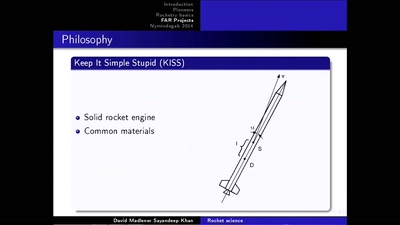
Rocket science – how hard can it be?
First steps into space with sounding rockets

61 min
Untrusting the CPU
A proposal for secure computing in an age where we cannot…

53 min
When algorithms fail in our personal lives
Social media break up coordinator
60 min
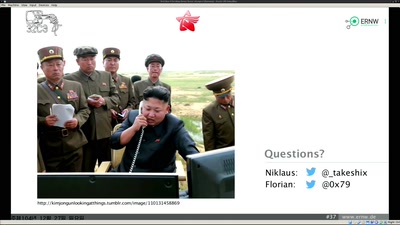
Lifting the Fog on Red Star OS
A deep dive into the surveillance features of North Korea's…

49 min
Toward a Cognitive "Quantified Self"
Activity Recognition for the Mind
56 min
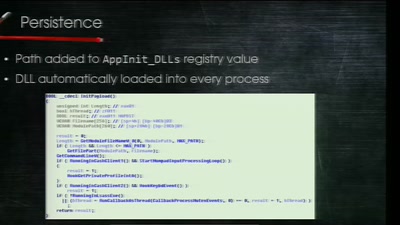
Electronic Bank Robberies
Stealing Money from ATMs with Malware
55 min
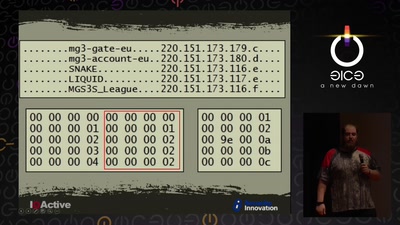
Cyber Necromancy
Reverse Engineering Dead Protocols
39 min
Transmission Control Protocol
TCP/IP basics

40 min
The Great Escape of ESXi
Breaking Out of a Sandboxed Virtual Machine
47 min
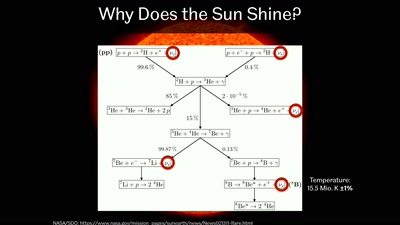
Going Deep Underground to Watch the Stars
Neutrino Astronomy with Hyper-Kamiokande

59 min
Provable Security
How I learned to stop worrying and love the backdoor

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…

65 min
The Untold Story of Edward Snowden’s Escape from Hong Kong
and How You Can Help the Refugees Who Saved His Life

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

54 min