Search for "m-1-k-3" returned 9403 results

48 min
Breaking WEP in less than 60 Seconds
the next level

54 min
Swedish analysis of Nazi crypto TTYs
How Beurling et al. broke the Siemens & Halske T52 crypto…

60 min
B.A.T.M.A.N. - Better Approach to Mobile Ad-Hoc Networking
New routing algorithm and daemon for wireless community…

55 min
Hack Your Brain
Using Sound & Light Machines to achieve desired states of…

47 min
WIPO Broadcasting Treaty
Lobbying on an International Scale

33 min
Enabling Innovation in Europe
Hacker Spaces, Startups, and a new approach to social…
41 min
Terrorists and the Internet
A Justification for Stricter Laws?
119 min
monochrom's Taugshow #12
A joyful bucket full of good clean fanaticism, crisis,…

51 min
The School of Hacking Art
Is it possible? 10 years experience from the first man who…

65 min
ZERT: VML, ANI and Third-party Patches
Assembly - lots of it.
79 min
Online Search
A Necessary Investigation Instrument?

44 min
GNU Radio & the Universal Software Radio Peripheral
Current Capabilities and Future Directions

43 min
Twisting timing in your favour
Finding and exploiting concurrency issues in software
56 min
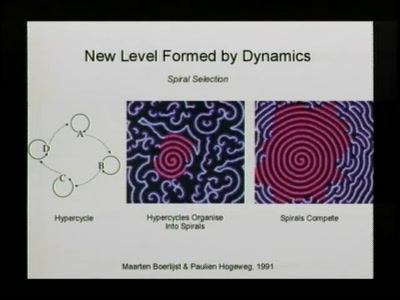
Life & Complexity
Organisation, information and optimisation in real and…
53 min
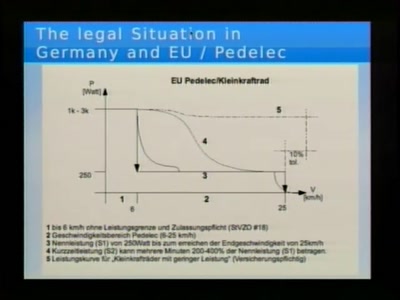
21st Century digital Bikes
No Gas, No Fee or Tax, No Driver License, what's possible…
41 min
Hacking on the Nanoscale
Dual Beam Devices for Rapid Prototyping and Reverse…

18 min
Camp Opening Event
Welcome!

59 min
Dungeons and Hyperlinks
Electronic Literature and Digital Narratives from Text…

38 min
People, Profiles and Trust
On interpersonal trust in web-mediated social spaces

64 min
Arguments Against Surveillance
'Cos "I Don't Like It" Is Not Enough!

53 min
A Case Against C++
Why C++ is bad for the environment, causes global warming…

37 min
Hacking Space
Cheap access to Space using lighter then air methods
46 min