Search for "m-1-k-3" returned 9403 results
62 min
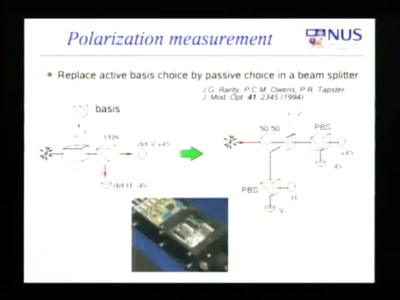
Relay attacks on card payment: vulnerabilities and defences
Keeping your enemies close
60 min
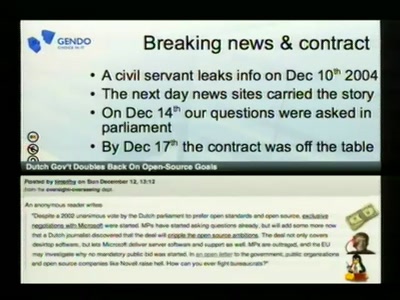
Open Source Lobbying, tips from the trenches
From one angry e-mail to writing national policy on open…

42 min
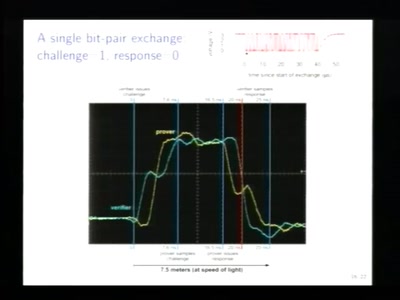
From Ring Zero to UID Zero
A couple of stories about kernel exploiting

63 min
Wireless Kernel Tweaking
or how B.A.T.M.A.N. learned to fly

65 min
Elektronische Dokumente und die Zukunft des Lesens
Warum es so ewig gedauert hat, bis Bücher auf geeigneten…
50 min
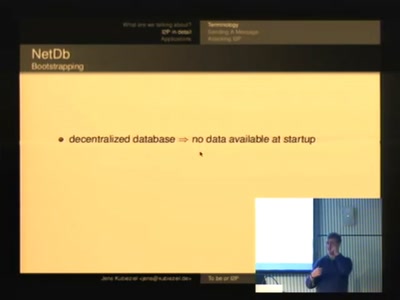
To be or I2P
An introduction into anonymous communication with I2P
51 min
After C: D, libd and the Slate project
A clean slate for operating systems
58 min
Linguistic Hacking
How to know what a text in an unknown language is about?

57 min
C64-DTV Hacking
Revisiting the legendary computer in a joystick

52 min
Modelling Infectious Diseases in Virtual Realities
The "corrupted blood" plague of WoW from an epidemiological…

42 min
Just in Time compilers - breaking a VM
Practical VM exploiting based on CACAO

39 min
DIY Survival
How to survive the apocalypse or a robot uprising
73 min
Das Panoptische Prinzip - Filme über die Zeit nach der Privatsphäre
Ergebnisse des Minutenfilmwettbewerbs des C4 und des Kölner…

42 min
Inside the Mac OS X Kernel
Debunking Mac OS Myths

59 min
Simulating the Universe on Supercomputers
The evolution of cosmic structure
59 min
It was a bad idea anyway...
The demise of electronic voting in The Netherlands

38 min
Steam-Powered Telegraphy
A League of Telextraordinary Gentlemen present the marvel…

50 min
Design Noir
The seedy underbelly of electronic engineering

58 min
Digital Sustainability
Scarcity is Entering the Net

71 min
What is terrorism?
And who is terrorising whom?

74 min
"I can count every star in the heavens above but I have no heart I can't fall in love…".
The image of computers in popular music

62 min