Search for "m-1-k-3" returned 9403 results
57 min
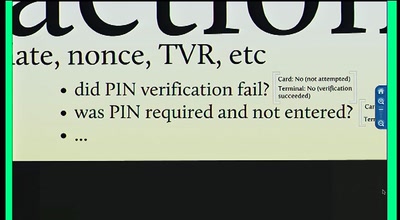
Chip and PIN is Broken
Vulnerabilities in the EMV Protocol
24 min
DIY synthesizers and sound generators
Where does the sound come from?

58 min
Is the SSLiverse a safe place?
An update on EFF's SSL Observatory project
66 min
The Baseband Apocalypse
all your baseband are belong to us
49 min
Lightning Talks - Day 2
4 minutes of fame
57 min
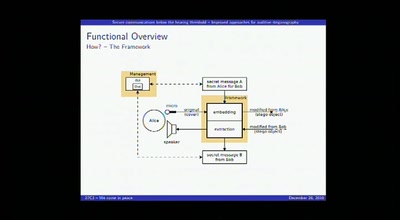
Secure communications below the hearing threshold
Improved approaches for auditive steganography

34 min
Lying To The Neighbours
Nasty effects with tracker-less BitTorrent

62 min
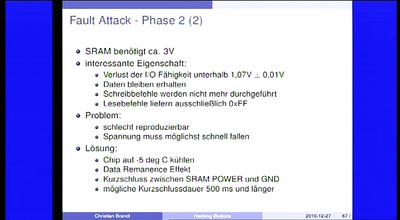
I Control Your Code
Attack Vectors Through the Eyes of Software-based Fault…
56 min
The importance of resisting Excessive Government Surveillance
Join me in exposing and challenging the constant violations…
49 min
A short political history of acoustics
For whom, and to do what, the science of sound was…
47 min
The Hidden Nemesis
Backdooring Embedded Controllers
51 min
File -> Print -> Electronics
A new circuit board printer will liberate you from the…

56 min
"The Concert"
a disconcerting moment for free culture

51 min
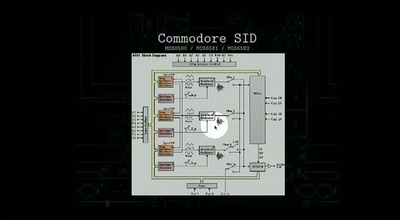
Reverse Engineering the MOS 6502 CPU
3510 transistors in 60 minutes

68 min
"Spoilers, Reverse Green, DECEL!" or "What's it doing now?"
Thoughts on the Automation and its Human interfaces on…

59 min
Part-Time Scientists
One year of Rocket Science!
56 min
Distributed FPGA Number Crunching For The Masses
How we obtained the equivalent power of a Deep Crack for a…
73 min
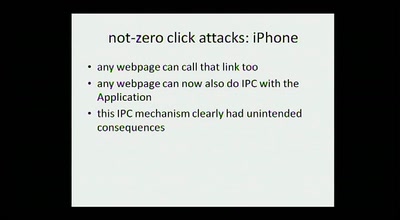
hacking smart phones
expanding the attack surface and then some
35 min
AllColoursAreBeautiful
interactive light installation inspired by blinkenlights

61 min
SMS-o-Death
From analyzing to attacking mobile phones on a large scale.

63 min