Search for "m-1-k-3" returned 9403 results

63 min
Print Me If You Dare
Firmware Modification Attacks and the Rise of Printer…

43 min
CCC Camp 2011 Video Impressions
Reviving a nice summer dream
53 min
The best of The oXcars
the greatest free/Libre culture show of all times
28 min
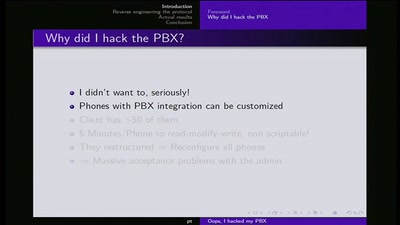
Ooops I hacked my PBX
Why auditing proprietary protocols matters
45 min
Implementation of MITM Attack on HDCP-Secured Links
A non-copyright circumventing application of the HDCP…

63 min
Power gadgets with your own electricity
escape the basement and make the sun work for you
40 min
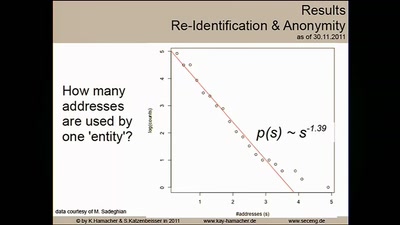
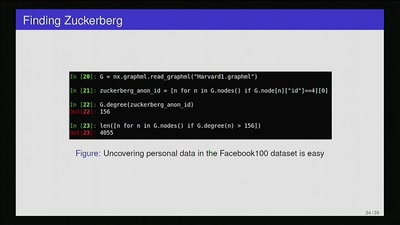
Privacy Invasion or Innovative Science?
Academia, social media data, and privacy

62 min
Post Memory Corruption Memory Analysis
Automating exploitation of invalid memory writes
56 min
Effective Denial of Service attacks against web application platforms
We are the 99% (CPU usage)

53 min
Building a Distributed Satellite Ground Station Network - A Call To Arms
Hackers need satellites. Hackers need internet over…
57 min
Hacking MFPs
Part2 - PostScript: Um, you've been hacked
116 min
Hacker Jeopardy
Number guessing for geeks
45 min
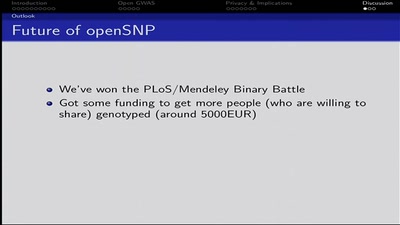
Crowdsourcing Genome Wide Association Studies
Freeing Genetic Data from Corporate Vaults

26 min
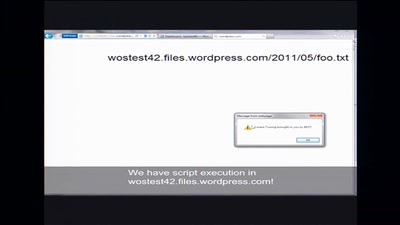
Don't scan, just ask
A new approach of identifying vulnerable web applications

57 min
7 years, 400+ podcasts, and a whole lot of Frequent Flyer Miles
Lessons learned from producing a weekly independent podcast…

56 min
Rootkits in your Web application
Achieving a permanent stealthy compromise of user accounts…

26 min
Data Mining the Israeli Census
Insights into a publicly available registry
61 min