Search for ".hev" returned 1880 results

30 min
The Machine To Be Another
Exploring identity and empathy through neuroscience,…

58 min
Baseband Exploitation in 2013
Hexagon challenges

57 min
TrustZone-M(eh): Breaking ARMv8-M's security
Hardware attacks on the latest generation of ARM Cortex-M…

69 min
Telescope Making
How to make your own telescope
60 min
Compileroptimierungen für Forth im Microcontroller
Mecrisp intern

60 min
Why is GPG "damn near unusable"?
An overview of usable security research
61 min
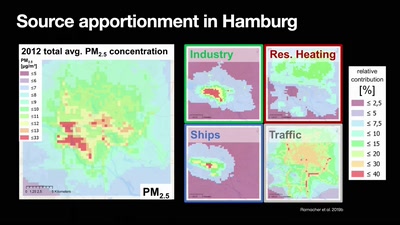
Numerical Air Quality Modeling Systems
a journey from emissions to exposure

60 min
Hacking Reality
Mixed Reality and multi-sensory communication

45 min
Offene Hör Muscheln
(OHM #019)
43 min
If It Ain't Broken, Do Fix It
Building Modern Cryptography

61 min
Correcting copywrongs
European copyright reform is finally on the horizon

58 min
How to Break PDFs
Breaking PDF Encryption and PDF Signatures
38 min
A deep dive into the world of DOS viruses
Explaining in detail just how those little COM files…

32 min