Search for "ultimate" returned 100 results

60 min
On the insecure nature of turbine control systems in power generation
A security study of turbine control systems in power…

42 min
Reverse engineering FPGAs
Dissecting FPGAs from bottom up, extracting schematics and…
47 min
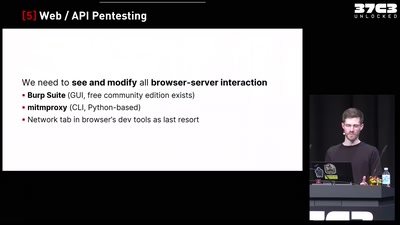
Finding Vulnerabilities in Internet-Connected Devices
A Beginner’s Guide
60 min
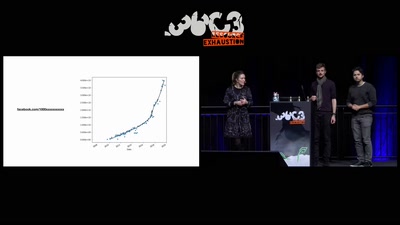
Inside the Fake Like Factories
How thousands of Facebook, You Tube and Instagram pages…

56 min
eMMC hacking, or: how I fixed long-dead Galaxy S3 phones
A journey on how to fix broken proprietary hardware by…
38 min
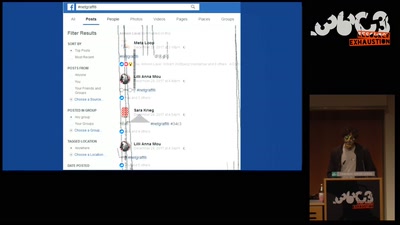
Unpacking the compromises of Aadhaar, and other digital identities inspired by it
Governments around the world are implementing digital…
40 min
Art against Facebook
Graffiti in the ruins of the feed and the…
32 min
library operating systems
reject the default reality^W abstractions and substitute…
32 min
Coding your body
How to decipher the messages of your body
61 min
How to Hack Your Way to Space
Bringing the Hacker Mindset to the Space Ecosphere - The…

32 min
Verified Firewall Ruleset Verification
Math, Functional Programming, Theorem Proving, and an…

31 min
The Clash of Digitalizations
The Devolution of Arab Men from Humans to Digital Fodder
61 min
Reconstructing game footage from a Game Boy's memory bus
The GB Interceptor
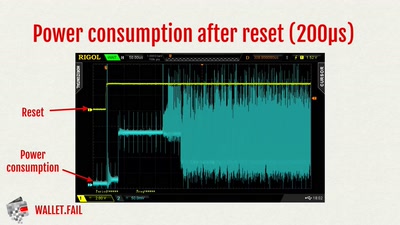
61 min




![Why we are addicted to lithium [2/2]](https://static.media.ccc.de/media/events/rc3/2021/194-17816a45-eea7-5b85-b623-5f343aec59de.jpg)