Search for "the ultimate" returned 107 results

60 min
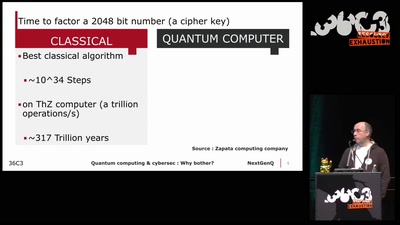
On the insecure nature of turbine control systems in power generation
A security study of turbine control systems in power…
60 min
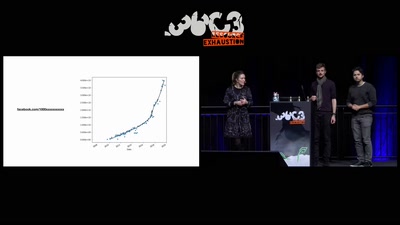
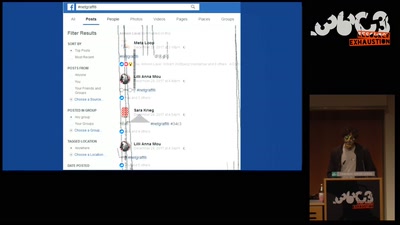
Inside the Fake Like Factories
How thousands of Facebook, You Tube and Instagram pages…
40 min
Art against Facebook
Graffiti in the ruins of the feed and the…
38 min
Unpacking the compromises of Aadhaar, and other digital identities inspired by it
Governments around the world are implementing digital…

42 min
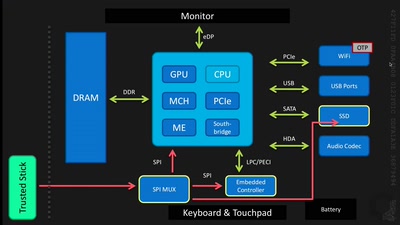
Reverse engineering FPGAs
Dissecting FPGAs from bottom up, extracting schematics and…

29 min
Perfect Paul
On Freedom of Facial Expression
61 min
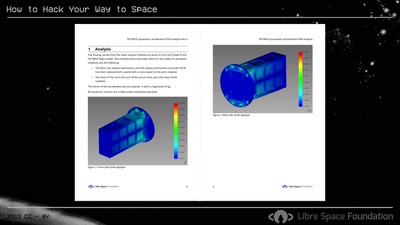
How to Hack Your Way to Space
Bringing the Hacker Mindset to the Space Ecosphere - The…

32 min
Verified Firewall Ruleset Verification
Math, Functional Programming, Theorem Proving, and an…
32 min
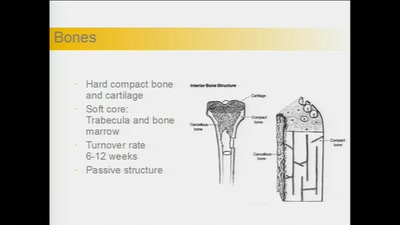
Coding your body
How to decipher the messages of your body
61 min
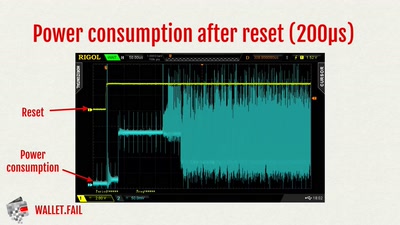
wallet.fail
Hacking the most popular cryptocurrency hardware wallets
47 min
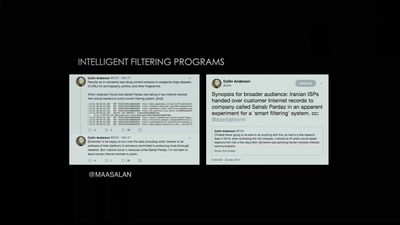
Tightening the Net in Iran
The Situation of Censorship and Surveillance in Iran, and…

56 min
eMMC hacking, or: how I fixed long-dead Galaxy S3 phones
A journey on how to fix broken proprietary hardware by…

60 min