Search for "scada" returned 82 results

32 min
The Case for Scale in Cyber Security
Security Track Keynote

44 min
What the cyberoptimists got wrong - and what to do about it
Tech unexeptionalism and the monopolization of every…

60 min
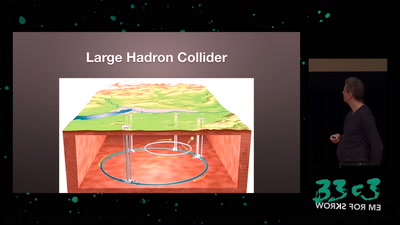
On the insecure nature of turbine control systems in power generation
A security study of turbine control systems in power…

53 min
Cryptography demystified
An introduction without maths

58 min
PLC-Blaster
Ein Computerwurm für PLCs

58 min
How to Break PDFs
Breaking PDF Encryption and PDF Signatures

40 min
An introduction to Firmware Analysis
Techniques - Tools - Tricks

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities
60 min
Unpatchable
Living with a vulnerable implanted device

62 min
Kyber and Post-Quantum Crypto
How does it work?
62 min
Getting software right with properties, generated tests, and proofs
Evolve your hack into robust software!
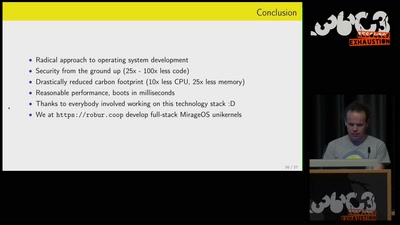
52 min
Leaving legacy behind
Reducing carbon footprint of network services with MirageOS…

51 min
Virtual Secure Boot
Secure Boot support in qemu, kvm and ovmf.

51 min