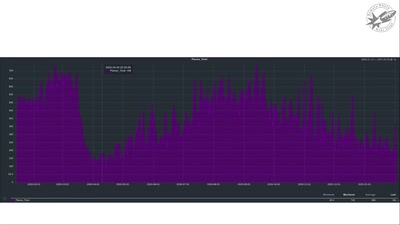
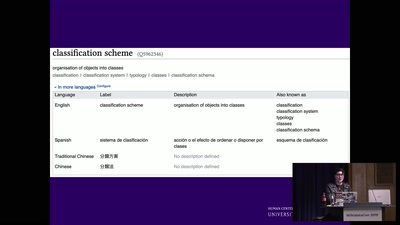
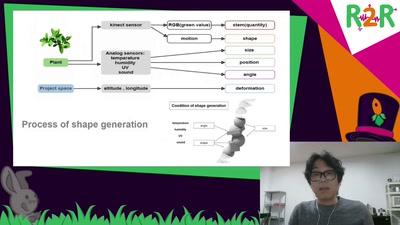
Search for "582" returned 1911 results

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

63 min
Analyze the Facebook algorithm and reclaim data sovereignty
Algorithms define your priorities. Who else besides you can…

37 min
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…

44 min
ASLR on the line
Practical cache attacks on the MMU

43 min
Scholz greift durch: Die AfD wird verboten - Deepfakes auch!
Das Zentrum für politische Schönheit und der Flyerservice…

50 min
Connected Mobility hacken: digital.bike.23
Von E-Bikes in der Connected Mobility zur Entstehung eines…

61 min
CAESAR and NORX
Developing the Future of Authenticated Encryption

42 min
Das FlipDot-Projekt
Spaß mit mechanischer Anzeige
49 min
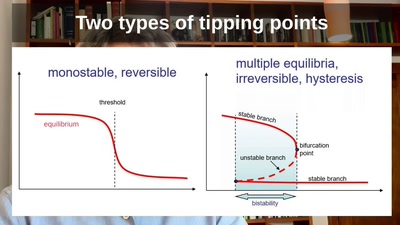

![Why we are addicted to lithium [2/2]](https://static.media.ccc.de/media/events/rc3/2021/194-17816a45-eea7-5b85-b623-5f343aec59de.jpg)