Search for "Remote" returned 1056 results

30 min
Forging the USB armory
Creating an open source secure flash-drive-sized computer

42 min
NEW IMPORTANT INSTRUCTIONS
Real-world exploits and mitigations in Large Language Model…
42 min
Domain Name System
Hierarchical decentralized naming system used since 30 years
62 min
Space Hacker
Uploading rover...

58 min
Baseband Exploitation in 2013
Hexagon challenges
61 min
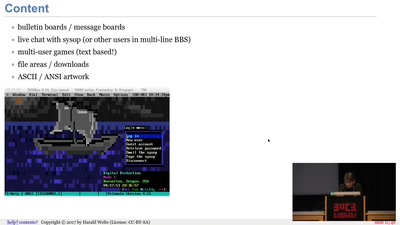
BBSs and early Internet access in the 1990ies
Modems, FIDO, Z-Netz, Usenet, UUCP, SLIP and ISDN

43 min
Deploy software with systemd-sysext
Introduction to OS extensions with sysext images

64 min
It Always Feels Like the Five Eyes Are Watching You
Five Eyes’ Quest For Security Has Given Us Widespread…
16 min