Search for "677" returned 1827 results

32 min
History and implications of DRM
From tractors to Web standards
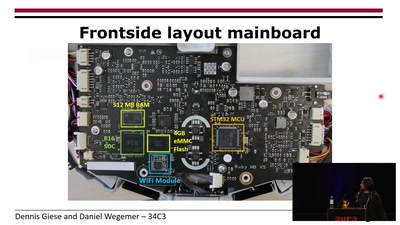
31 min
Unleash your smart-home devices: Vacuum Cleaning Robot Hacking
Why is my vacuum as powerful as my smartphone?

32 min
Technology and Mass Atrocity Prevention
Overview on Current Efforts - We Need Moar H4x0rs?!
31 min
GIFs: Tod eines Mediums. Und sein Leben nach dem Tod.
Wie es kommt, dass technischer Fortschritt den Nutzern…

30 min
Forging the USB armory
Creating an open source secure flash-drive-sized computer

32 min
Modern key distribution with ClaimChain
A decentralized Public Key Infrastructure that supports…

46 min
Electronic Evicence in Criminal Matters
An introduction and critique of the EC proposal for a…

51 min
Virtual Secure Boot
Secure Boot support in qemu, kvm and ovmf.

63 min
A look into the Mobile Messaging Black Box
A gentle introduction to mobile messaging and subsequent…

49 min
Dissecting VoLTE
Exploiting Free Data Channels and Security Problems

41 min
Extracting keys from FPGAs, OTP Tokens and Door Locks
Side-Channel (and other) Attacks in Practice

58 min
Switches Get Stitches
Industrial System Ownership

30 min
OONI: Let's Fight Internet Censorship, Together!
The Open Observatory of Network Interference
31 min
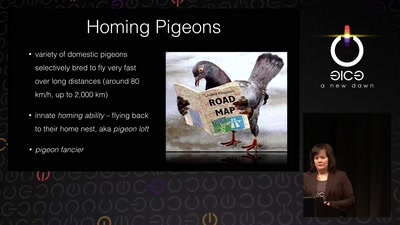
Living Drones
From war pigeons in 1914 to cyborg moths in 2014

29 min
Infocalypse now: P0wning stuff is not enough
Several failure modes of the hacker scene

57 min





![failed: [Inklusion]](https://static.media.ccc.de/media/conferences/divoc/r2r/7-28904449-d357-566f-97ef-86ade89f9395.jpg)