Search for "Twi"
prev
next

46 min
--Gaining code execution using a malicious SQLite database

60 min
from key distribution to position-based cryptography
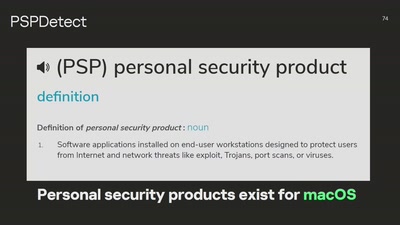
58 min
What You Get When Attack iPhones of Researchers

60 min
Autonomous flying vehicles, where are we and where are we…

40 min
Techniques - Tools - Tricks

32 min
Automatic detection of key-reuse vulnerabilities
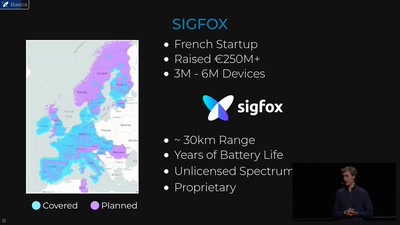
38 min
Dissecting the radio protocol of Sigfox, the global…
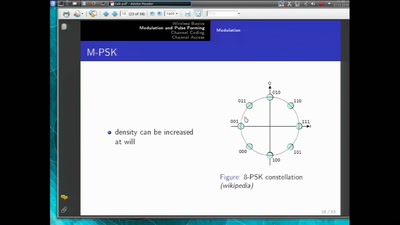
46 min
introduction to software radio principles

29 min
Wireless Physical Layer Security & More...
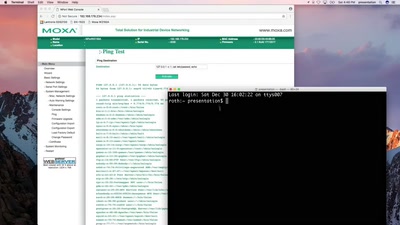
45 min
Hacking industrial control gateways
prev
next




