Search for "629" returned 1893 results

42 min
A world without blockchain
How (inter)national money transfers works

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

33 min
UPSat - the first open source satellite
Going to space the libre way
35 min
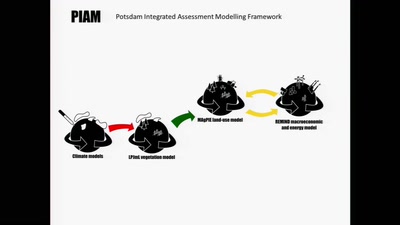
Simulating the future of the global agro-food system
Cybernetic models analyze scenarios of interactions between…
41 min
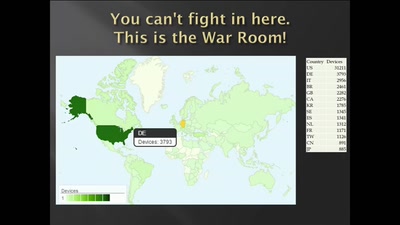
SCADA StrangeLove 2
We already know

32 min
Craft, leisure, and end-user innovation
How hacking is conceived in social science research

30 min
On Computing Numbers, with an Application to Problems of our Society
Journalism ♥ Computer Science
36 min
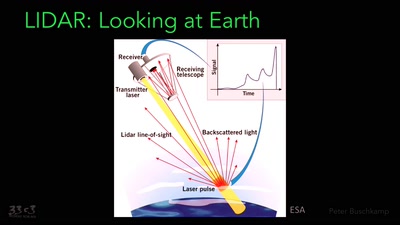
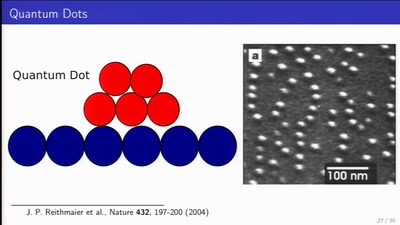
Long Distance Quantum Communication
Concepts and components for intercontinal communication…

27 min
ANIMAL()CITY
Unleashed!
40 min
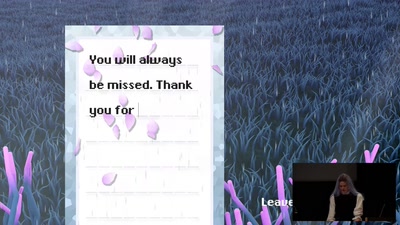
Never Forgetti
a didactic live-gaming performance about dying women across…
31 min
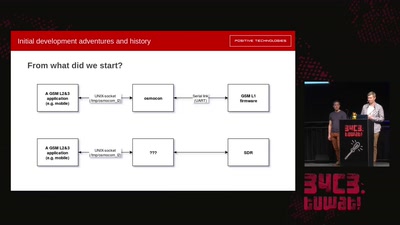
Running GSM mobile phone on SDR
SDR PHY for OsmocomBB

24 min
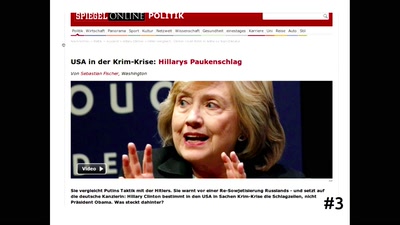
Die netzpolitische Neujahrsansprache
Digitalisierung - Ja, wir schaffen das!

31 min
Buffered Daemons
Sound art performance exploring the concept of translation…
60 min
Das Zahnrad aus Fleisch
Expeditionen ins Kommentierreich

37 min
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…

33 min
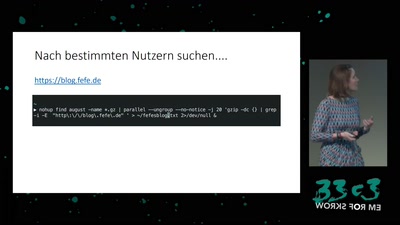
Retail Surveillance / Retail Countersurveillance
50 most unwanted retail surveillance technologies / 50 most…
60 min