Search for "OCs of 35C3"
prev
next

16 min
Bypassing Enterprise Policy in Firefox
45 min
Hacking industrial control gateways
36 min
Analyzing Embedded OS Random Number Generators

62 min
The militarization of the Internet
58 min
What You Get When Attack iPhones of Researchers

30 min
Journalism ♥ Computer Science
61 min
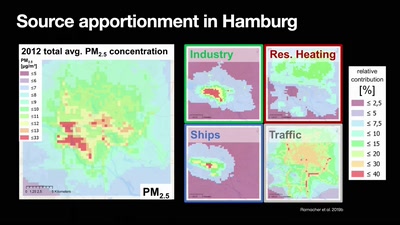
a journey from emissions to exposure
55 min
Preserving access to the open Internet with circumvention…

51 min
Secure Boot support in qemu, kvm and ovmf.

61 min
Developing the Future of Authenticated Encryption
prev
next

