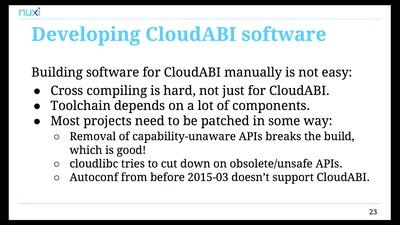
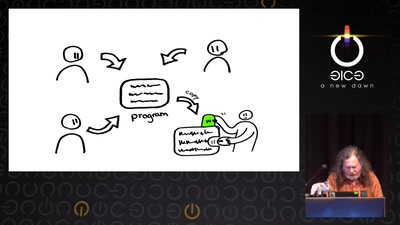
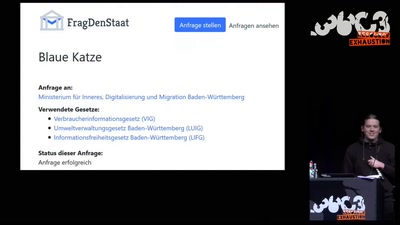
Search for "Jens" returned 477 results

64 min
"Exploit" in theater
post-existentialism is the question, not post-privacy

59 min
Hacking EU funding for a decentralizing FOSS project
Understanding and adapting EU legal guidelines from a FOSS…

57 min
Kryptographie nach Snowden
Was tun nach der mittelmäßigen Kryptographie-Apokalypse?
62 min
SuperMUC-NG
… und das Rennen um den schnellsten Computer der Welt
56 min
Rock' em Graphic Cards
Introduction to Heterogeneous Parallel Programming
95 min
Hacker Jeopardy
Zahlenraten für Geeks

61 min
Deploying TLS 1.3: the great, the good and the bad
Improving the encrypted the web, one round-trip at a time

61 min
Correcting copywrongs
European copyright reform is finally on the horizon

59 min
Fernvale: An Open Hardware and Software Platform, Based on the (nominally) Closed-Source…
A Lawful Method for Converting Closed IP into Open IP

60 min
The Exploration and Exploitation of an SD Memory Card
by xobs & bunnie

60 min
Everything you always wanted to know about Certificate Transparency
(but were afraid to ask)

64 min
We only have one earth
A case for expansionistic space policy

37 min
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…

126 min