Search for "N-te" returned 8901 results

49 min
MySQL Multi-Master Replication Failover - A step-by-step explanation
How to setup a MySQL cluster with Automatic failover for HA
64 min
Are Whistleblowers safer today than they were at OHM2013?
Current case studies of whistleblowing in Europe, and how…
42 min
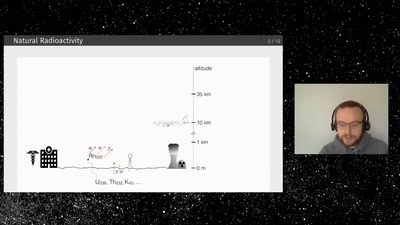
Measuring radioactivity using low-cost silicon sensors
A DIY particle physics detector in a tin box.

61 min
Human body as an electric IO system
Hacking your brain, and other body parts. Debunking myths…

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…

51 min
The JPEG is dead! Long live the JPEG!
A tour de force of major developments in open source image…
58 min
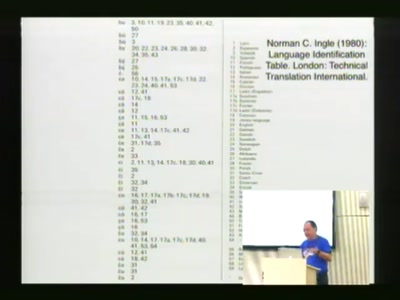
Linguistic Hacking
How to know what a text in an unknown language is about?

62 min
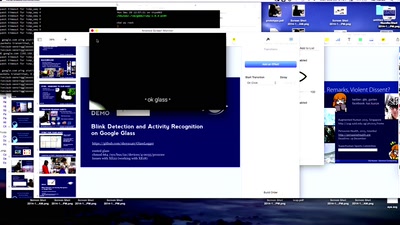
Post Memory Corruption Memory Analysis
Automating exploitation of invalid memory writes
32 min