Search for "zem" returned 4002 results

55 min
Inside Field Station Berlin Teufelsberg
The story of the NSA listening post – told by an ex-SIGINT…
58 min
RFID Treehouse of Horror
Hacking City-Wide Access Control Systems
38 min
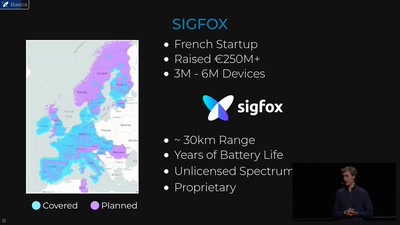
Hunting the Sigfox: Wireless IoT Network Security
Dissecting the radio protocol of Sigfox, the global…

54 min
Kernel Tracing With eBPF
Unlocking God Mode on Linux

57 min
Everything you want to know about x86 microcode, but might have been afraid to ask
An introduction into reverse-engineering x86 microcode and…

58 min
Glitching For n00bs
A Journey to Coax Out Chips' Inner Secrets

58 min
When hardware must „just work“
An inside look at x86 CPU design

61 min
Untrusting the CPU
A proposal for secure computing in an age where we cannot…

58 min
Virtual Machine Introspection
From the Outside Looking In
38 min
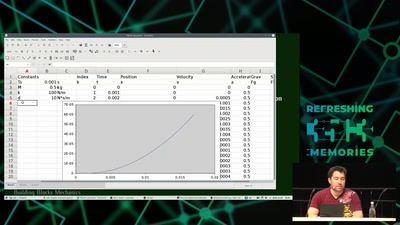
Modeling and Simulation of Physical Systems for Hobbyists
Essential Tools for Developing, Testing and Debugging…

63 min
goto fail;
exploring two decades of transport layer insecurity
62 min
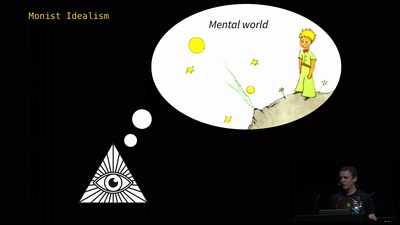
The Ghost in the Machine
An Artificial Intelligence Perspective on the Soul

41 min
Extracting keys from FPGAs, OTP Tokens and Door Locks
Side-Channel (and other) Attacks in Practice

60 min