Search for "id4=WPnt" returned 320 results
61 min
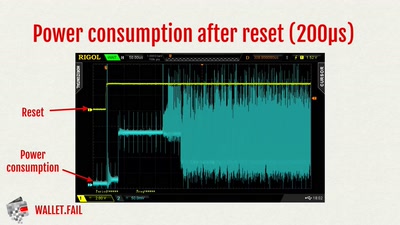
wallet.fail
Hacking the most popular cryptocurrency hardware wallets

63 min
Analyze the Facebook algorithm and reclaim data sovereignty
Algorithms define your priorities. Who else besides you can…
58 min
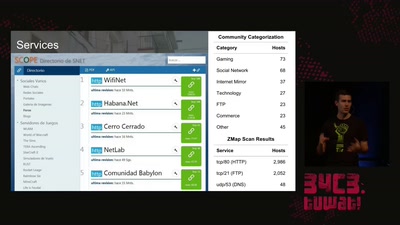
The Internet in Cuba: A Story of Community Resilience
Get a unique tour of some of the world’s most unusual…

58 min
Thwarting Evil Maid Attacks
Physically Unclonable Functions for Hardware Tamper…

55 min
Fuzzing the phone in the iPhone
D-d-d-di-di-d-d-di-d-di-d-di-d-dimm!

58 min
Self-encrypting deception
weaknesses in the encryption of solid state drives (SSDs)

59 min
Fernvale: An Open Hardware and Software Platform, Based on the (nominally) Closed-Source…
A Lawful Method for Converting Closed IP into Open IP

59 min
TamaGo - bare metal Go framework for ARM SoCs.
Reducing the attack surface with pure embedded Go.
61 min
Rocket Kitten: Advanced Off-the-Shelf Targeted Attacks Against Nation States
A Deep Technical Analysis
61 min
Avoiding kernel panic: Europe’s biggest fails in digital policy-making
How the institutions fuck up, and how we fuck it up as well

54 min
Tactical Embodiment
Activism and Performance In Hostile Spaces Online
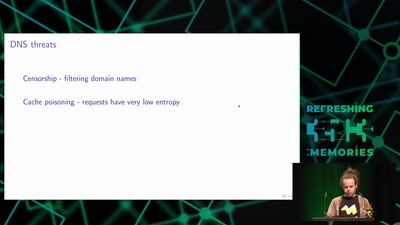
42 min