Search for person "Johan Van de Wauw" returned 186 results
49 min
Scanning and reporting vulnerabilities for the whole IPv4 space.
How the Dutch Institute for Vulnerability Disclosure scales…
87 min
DNS privacy and security
Chaos Colloquium #1

53 min
Smart, safe & happy
ensuring civil rights in the digital era
47 min
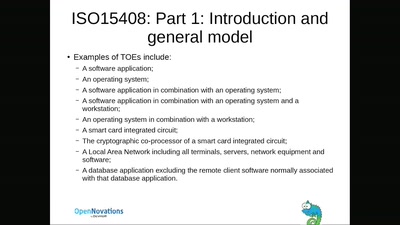
The new EU CyberSecurity Act
Or how to prevent the EU from becoming the worlds largest…
63 min
LightKultur in Deutschland
Clubkultur oder wie modern ist unser Kulturbegriff?

32 min