Search for "10" returned 5232 results

60 min
HAL - The Open-Source Hardware Analyzer
A dive into the foundations of hardware reverse engineering…

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…

46 min
Taking a scalpel to QNX
Analyzing & Breaking Exploit Mitigations and Secure Random…

59 min
Hardsploit: A Metasploit-like tool for hardware hacking
A complete toolbox for IoT security
40 min
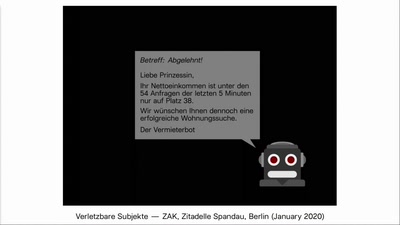
Wohnungsbot: An Automation-Drama in Three Acts
A media-art project which automates the search for flats in…

58 min
Decoding Contactless (Card) Payments
An Exploration of NFC Transactions and Explanation How…

59 min
Memory Deduplication: The Curse that Keeps on Giving
A tale of 3 different memory deduplication based…

57 min
How I Learned to Stop Reinventing and Love the Wheels
or having FUN with (home/hackerspace) robotics

55 min
White-Box Cryptography
Survey

60 min
Beyond Anti Evil Maid
Making it easier to avoid low-level compromise, and why…

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data

60 min












