Search for "10" returned 5221 results

58 min
When hardware must „just work“
An inside look at x86 CPU design

64 min
Magic Lantern
Free Software on Your Camera

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…

58 min
Decoding Contactless (Card) Payments
An Exploration of NFC Transactions and Explanation How…

59 min
Memory Deduplication: The Curse that Keeps on Giving
A tale of 3 different memory deduplication based…

57 min
How I Learned to Stop Reinventing and Love the Wheels
or having FUN with (home/hackerspace) robotics

55 min
White-Box Cryptography
Survey

60 min
Beyond Anti Evil Maid
Making it easier to avoid low-level compromise, and why…

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data

58 min
Thwarting Evil Maid Attacks
Physically Unclonable Functions for Hardware Tamper…
62 min
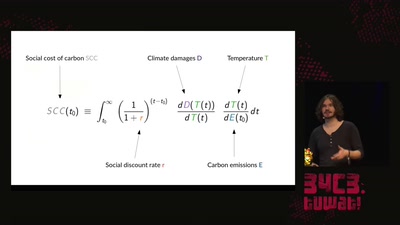
A hacker's guide to Climate Change - What do we know and how do we know it?
An introduction to the basics of climate research and what…

61 min
Die dreckige Empirie
Kann man empirischen Studien trauen?

62 min
The Price Of Dissent
The surveillance state & modern day COINTELPRO tactics
95 min