Search for "15" returned 4954 results
62 min
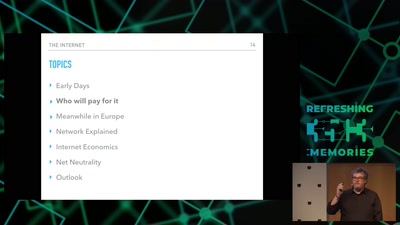
Internet, the Business Side
a try to explain the ecosystem

59 min
Hardsploit: A Metasploit-like tool for hardware hacking
A complete toolbox for IoT security

30 min
The Machine To Be Another
Exploring identity and empathy through neuroscience,…
60 min
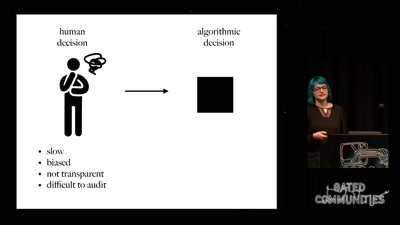
Prediction and Control
Watching Algorithms
47 min
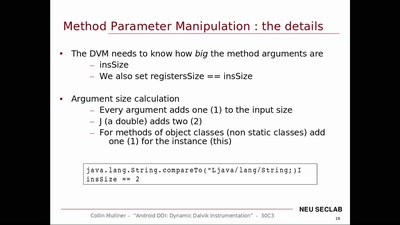
Android DDI
Dynamic Dalvik Instrumentation of Android Applications and…

61 min
An Elevator to the Moon (and back)
Space Transportation and the Extraterrestrial Imperative
40 min
No roborders, no nation, or: smile for a European surveillance propagation
How an agency implements Fortress Europe by degrading…

45 min
To Protect And Infect
The militarization of the Internet

40 min
Radical Digital Painting
Fantastic Media Manipulation

59 min
Zwischen supersicherer Verschlüsselung und Klartext liegt nur ein falsches Bit
Ein Streifzug durch die Fehler in der Kryptografie

57 min
Kryptographie nach Snowden
Was tun nach der mittelmäßigen Kryptographie-Apokalypse?
50 min
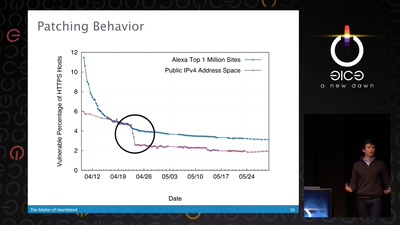
The Matter of Heartbleed
What went wrong, how the Internet reacted, what we can…

59 min
Hacking EU funding for a decentralizing FOSS project
Understanding and adapting EU legal guidelines from a FOSS…

55 min