Search for "16" returned 4670 results

53 min
When algorithms fail in our personal lives
Social media break up coordinator

62 min
The Internet (Doesn't) Need Another Security Guide
Creating Internet Privacy and Security Resources That Don't…
60 min
„Nach bestem Wissen und Gewissen“ – Floskeln in der Politik
Politische Phrasologie – warum man aus dem ganzen Zeug, das…

54 min
How hackers grind an MMORPG: by taking it apart!
An introduction to reverse engineering network protocols

48 min
REXUS/BEXUS - Rocket and Balloon Experiments for University Students
How to bring student experiments into space.

61 min
Ten years after ‚We Lost The War‘
The future does not look much brighter than ten years ago.…
64 min
Der Deep Learning Hype
Wie lange kann es so weitergehen?
58 min
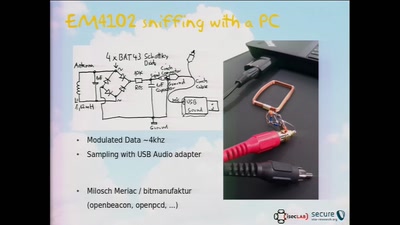
RFID Treehouse of Horror
Hacking City-Wide Access Control Systems
91 min
What the World can learn from Hongkong
From Unanimity to Anonymity

58 min
Self-encrypting deception
weaknesses in the encryption of solid state drives (SSDs)
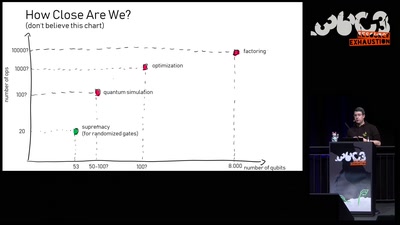
61 min
Quantum Computing: Are we there yet?
An introduction to quantum computing and a review of the…

57 min
Du kannst alles hacken – du darfst dich nur nicht erwischen lassen.
OpSec für Datenreisende

39 min
Web-based Cryptojacking in the Wild
When your browser is mining coins for other people

66 min
Keine Anhaltspunkte für flächendeckende Überwachung
Die Diskussion um NSA, PRISM, Tempora sprachlich und…

54 min
How (not) to build autonomous robots
Fables from building a startup in Silicon Valley

62 min








