Search for "27" returned 4134 results
55 min
Cat & Mouse: Evading the Censors in 2018
Preserving access to the open Internet with circumvention…
40 min
No roborders, no nation, or: smile for a European surveillance propagation
How an agency implements Fortress Europe by degrading…
41 min
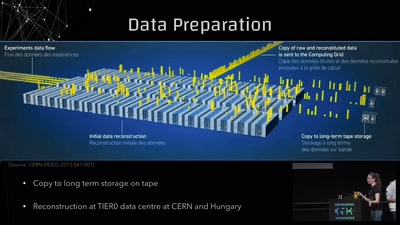
Conquering Large Numbers at the LHC
From 1 000 000 000 000 000 to 10: Breaking down 14 Orders…
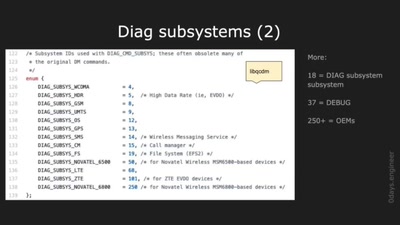
66 min
Advanced Hexagon Diag
Harnessing diagnostics for baseband vulnerability research

59 min
TamaGo - bare metal Go framework for ARM SoCs.
Reducing the attack surface with pure embedded Go.

51 min
Smart Home - Smart Hack
Wie der Weg ins digitale Zuhause zum Spaziergang wird
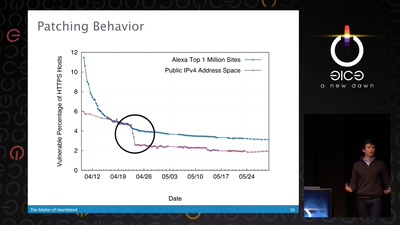
50 min
The Matter of Heartbleed
What went wrong, how the Internet reacted, what we can…

59 min
Hacking EU funding for a decentralizing FOSS project
Understanding and adapting EU legal guidelines from a FOSS…

60 min
The rise and fall of Internet voting in Norway
Evaluating a complex cryptographic implementation

64 min
"Exploit" in theater
post-existentialism is the question, not post-privacy
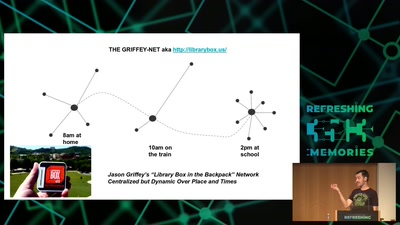
60 min
Wind: Off-Grid Services for Everyday People
Integrating nearby and offline connectivity with the…

57 min
Kryptographie nach Snowden
Was tun nach der mittelmäßigen Kryptographie-Apokalypse?

62 min
radare demystified
after 1.0

63 min



![Wie man zu[mr] System Ingenieur(in)? wird](https://static.media.ccc.de/media/events/rc3/133-ed57ba19-7686-55a9-b228-38c5a10b444b.jpg)