Search for "18" returned 4659 results

59 min
Memory Deduplication: The Curse that Keeps on Giving
A tale of 3 different memory deduplication based…

58 min
Baseband Exploitation in 2013
Hexagon challenges

60 min
Concepts for global TSCM
getting out of surveillance state mode

60 min
Beyond Anti Evil Maid
Making it easier to avoid low-level compromise, and why…

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data

60 min
Everything you always wanted to know about Certificate Transparency
(but were afraid to ask)

58 min
Überwachen und Sprache
How to do things with words
31 min
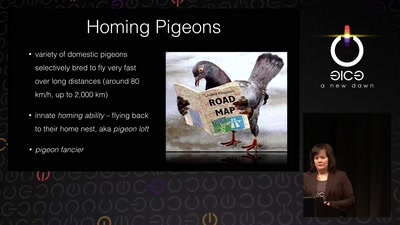
Living Drones
From war pigeons in 1914 to cyborg moths in 2014

63 min
Dissecting HDMI
Developing open, FPGA-based capture hardware for conference…

29 min
Infocalypse now: P0wning stuff is not enough
Several failure modes of the hacker scene
31 min
Media Disruption Led By The Blind
Hacking Visual Culture

58 min
When hardware must „just work“
An inside look at x86 CPU design

60 min