Search for "30" returned 4248 results

34 min
Ling - High level system programming
modular and precise resource management

60 min
Glass Hacks
Fun and frightening uses of always-on camera enabled…

61 min
CAESAR and NORX
Developing the Future of Authenticated Encryption

62 min
Let's Encrypt
A Free Robotic Certificate Authority

58 min
Protecting Your Privacy at the Border
Traveling with Digital Devices in the Golden Age of…

55 min
The Gospel of IRMA
Attribute Based Credentials in Practice

60 min
The Exploration and Exploitation of an SD Memory Card
by xobs & bunnie

59 min
Security of the IC Backside
The future of IC analysis

35 min
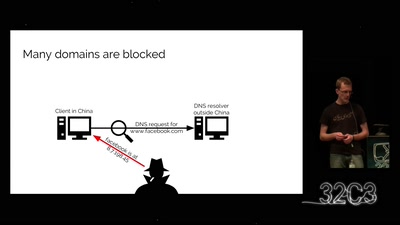
Harry Potter and the Not-So-Smart Proxy War
Taking a look at a covert CIA virtual fencing solution

60 min
Quantum Cryptography
from key distribution to position-based cryptography

33 min
Turing Complete User
What can be done to protect the term, the notion and the…

60 min