Search for "33" returned 3656 results
48 min
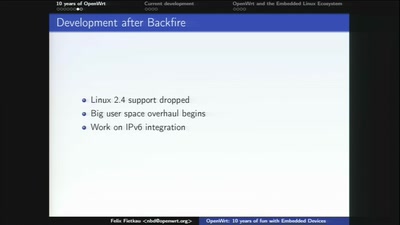
10 Years of Fun with Embedded Devices
How OpenWrt evolved from a WRT54G firmware to an universal…

54 min
How hackers grind an MMORPG: by taking it apart!
An introduction to reverse engineering network protocols

63 min
The Cloud Conspiracy 2008-2014
how the EU was hypnotised that the NSA did not exist

61 min
Untrusting the CPU
A proposal for secure computing in an age where we cannot…

62 min
Superheroes Still Need Phoneboxes
The art of making a free phonebox and the culture of…
35 min
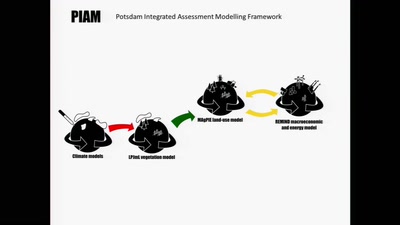
Simulating the future of the global agro-food system
Cybernetic models analyze scenarios of interactions between…

62 min
The Internet (Doesn't) Need Another Security Guide
Creating Internet Privacy and Security Resources That Don't…

60 min
From Computation to Consciousness
How computation helps to explain mind, universe and…

60 min
Best of Informationsfreiheit
Transparenz mit der Brechstange

53 min
No Love for the US Gov.
Why Lauri Love’s case is even more important than you…

60 min
Check your privileges!
How to drop more of your privileges to reduce attack…

60 min
Sneaking In Network Security
Enforcing strong network segmentation, without anyone…

54 min
Kernel Tracing With eBPF
Unlocking God Mode on Linux
64 min