Search for "25" returned 4577 results

49 min
Toward a Cognitive "Quantified Self"
Activity Recognition for the Mind

51 min
Uncovering vulnerabilities in Hoermann BiSecur
An AES encrypted radio system

51 min
Ecuador: how an authoritarian government is fooling the entire world
Guess what? The Government of Rafael Correa actually is…

59 min
Fernvale: An Open Hardware and Software Platform, Based on the (nominally) Closed-Source…
A Lawful Method for Converting Closed IP into Open IP

59 min
Security of the IC Backside
The future of IC analysis

61 min
Die dreckige Empirie
Kann man empirischen Studien trauen?

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…

61 min
Dead Man Edition
Auf dem Weg zu fairer Elektronik am Beispiel der Elkos …

60 min
Quantum Cryptography
from key distribution to position-based cryptography

60 min
The Fight for Encryption in 2016
Crypto fight in the Wake of Apple v. FBI
62 min
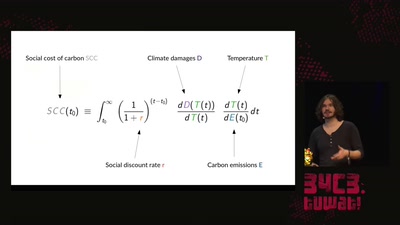
A hacker's guide to Climate Change - What do we know and how do we know it?
An introduction to the basics of climate research and what…
61 min
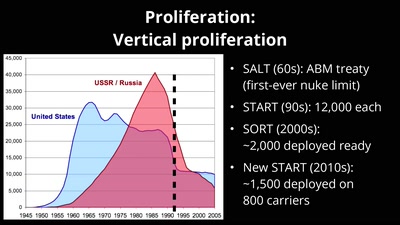
What Ever Happened to Nuclear Weapons?
Politics and Physics of a Problem That's Not Going Away

62 min
The Price Of Dissent
The surveillance state & modern day COINTELPRO tactics
61 min
Rocket Kitten: Advanced Off-the-Shelf Targeted Attacks Against Nation States
A Deep Technical Analysis

60 min
Internet Cube
Let's Build together a Free, Neutral and Decentralized…

22 min