Search for "25" returned 4577 results

49 min
Toward a Cognitive "Quantified Self"
Activity Recognition for the Mind

51 min
Uncovering vulnerabilities in Hoermann BiSecur
An AES encrypted radio system

59 min
Fernvale: An Open Hardware and Software Platform, Based on the (nominally) Closed-Source…
A Lawful Method for Converting Closed IP into Open IP

51 min
Ecuador: how an authoritarian government is fooling the entire world
Guess what? The Government of Rafael Correa actually is…

59 min
Security of the IC Backside
The future of IC analysis

61 min
Die dreckige Empirie
Kann man empirischen Studien trauen?

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…

60 min
Quantum Cryptography
from key distribution to position-based cryptography

61 min
Dead Man Edition
Auf dem Weg zu fairer Elektronik am Beispiel der Elkos …
61 min
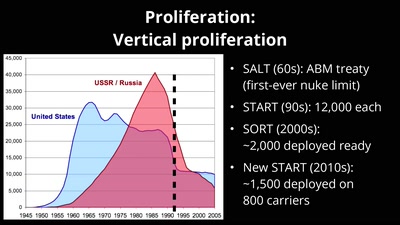
What Ever Happened to Nuclear Weapons?
Politics and Physics of a Problem That's Not Going Away

60 min

![Malte über das Logo der NooK 2023 [5 Minuten Termine auf dem CCCamp23]](https://static.media.ccc.de/media/regional/luebeck/chaotikum/1462-e02ac081-c997-4db2-a713-460a83446d47.jpg)
![Scammo über Pretty Good Proposal [5 Minuten Termine auf dem CCCamp23]](https://static.media.ccc.de/media/regional/luebeck/chaotikum/1460-32fa8ac7-7b3d-4e63-b706-83298ffea401.jpg)
![Leo über LuxMux [5 Minuten Termine auf dem CCCamp23]](https://static.media.ccc.de/media/regional/luebeck/chaotikum/1464-ff505d73-dbfb-4a59-a309-15fe8b8fad6d.jpg)
![Neocturne über MinedMap [5 Minuten Termine auf dem CCCamp23]](https://static.media.ccc.de/media/regional/luebeck/chaotikum/1463-5b948684-e02b-454a-8b04-30f081e84355.jpg)
![Philipp über FoodCoops [5 Minuten Termine auf dem CCCamp23]](https://static.media.ccc.de/media/regional/luebeck/chaotikum/1455-c5fb74e6-9137-4bfc-95a2-9d5416502b13.jpg)
![Falko über 3D Druck für Kinder [5 Minuten Termine auf dem CCCamp23]](https://static.media.ccc.de/media/regional/luebeck/chaotikum/1459-803723ae-9b8e-4d04-96f0-bb231577da0a.jpg)
![Liz über WireGuard [5 Minuten Termine auf dem CCCamp23]](https://static.media.ccc.de/media/regional/luebeck/chaotikum/1465-5e61d155-87ec-41be-85d0-c7d7be694dd9.jpg)