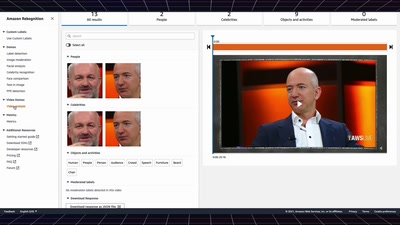
Search for "19" returned 4626 results
35 min
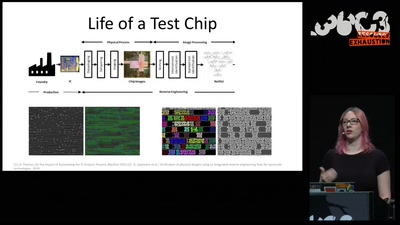
Understanding millions of gates
Introduction to IC reverse engineering for…
35 min
hacking disaster
mit Krisenintervention den Kapitalismus hacken

32 min
Why Do We Anthropomorphize Computers?...
...and dehumanize ourselves in the process?

29 min
2 Takte später
30C3S SCE mbH: GEMA-Konkurrenz für Fortgeschrittene

43 min
Forensic Architecture
Forensic Architecture is an independent research agency…

51 min
Virtual Secure Boot
Secure Boot support in qemu, kvm and ovmf.
61 min
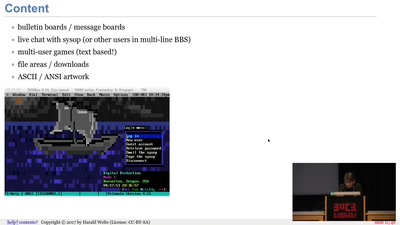
BBSs and early Internet access in the 1990ies
Modems, FIDO, Z-Netz, Usenet, UUCP, SLIP and ISDN
47 min
Hillbilly Tracking of Low Earth Orbit
Repurposing an Inmarsat Dish
56 min
Iridium Update
more than just pagers

33 min
institutions for Resolution Disputes
Rosa Menkman investigates video compression, feedback, and…
60 min
Katastrophe und Kommunikation am Beispiel Nord-Ost-Syrien
Humanitäre Hilfe zwischen Propaganda, Information und…

49 min
Dissecting VoLTE
Exploiting Free Data Channels and Security Problems

38 min
Schnaps Hacking
from apple to schnaps -- a complete diy-toolchain

41 min