Search for "11" returned 4565 results

58 min
Baseband Exploitation in 2013
Hexagon challenges

55 min
White-Box Cryptography
Survey

58 min
When hardware must „just work“
An inside look at x86 CPU design

57 min
How I Learned to Stop Reinventing and Love the Wheels
or having FUN with (home/hackerspace) robotics

60 min
Concepts for global TSCM
getting out of surveillance state mode

60 min
Beyond Anti Evil Maid
Making it easier to avoid low-level compromise, and why…

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data
38 min
Policing the Romantic Crowd
Velocipedes and Face Recognition
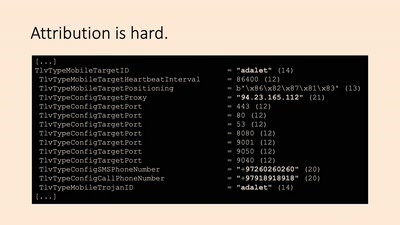
59 min
Finfisher verklagen
Rechtsbrüche beim Export von Überwachungssoftware

61 min
Net Neutrality in Europe
alea iacta est
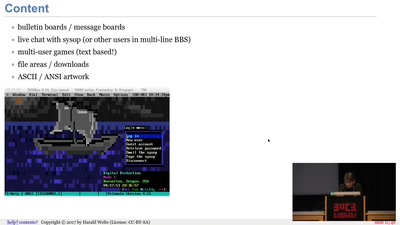
61 min
BBSs and early Internet access in the 1990ies
Modems, FIDO, Z-Netz, Usenet, UUCP, SLIP and ISDN

30 min
Privacy and Consumer Markets
Reversing the Surveillance Business Model

64 min
Technical aspects of the surveillance in and around the Ecuadorian embassy in London
Details about the man hunt for Julian Assange and Wikileaks

49 min
Dissecting VoLTE
Exploiting Free Data Channels and Security Problems

51 min
Virtual Secure Boot
Secure Boot support in qemu, kvm and ovmf.

46 min