Search for "75" returned 3170 results
41 min
SCADA StrangeLove 2
We already know

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

32 min
History and implications of DRM
From tractors to Web standards

32 min
Technology and Mass Atrocity Prevention
Overview on Current Efforts - We Need Moar H4x0rs?!
31 min
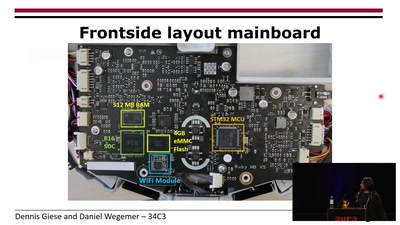
Unleash your smart-home devices: Vacuum Cleaning Robot Hacking
Why is my vacuum as powerful as my smartphone?
31 min
GIFs: Tod eines Mediums. Und sein Leben nach dem Tod.
Wie es kommt, dass technischer Fortschritt den Nutzern…

30 min
Forging the USB armory
Creating an open source secure flash-drive-sized computer

30 min
libusb: Maintainer fail
How I failed to run an open source project

101 min
Security Nightmares
Damit Sie auch morgen schlecht von Ihrem Computer träumen.

59 min
Die Sprache der Populisten
Wie politische "Gewissheiten" sprachlich konstruiert werden
42 min
Wifibroadcast
How to convert standard wifi dongles into digital broadcast…

38 min
Content take-downs: Who cleans the internet?
EU plans to swipe our freedom of expression under the carpet

32 min
Craft, leisure, and end-user innovation
How hacking is conceived in social science research
31 min