Search for "68" returned 2878 results

46 min
Electronic Evicence in Criminal Matters
An introduction and critique of the EC proposal for a…

41 min
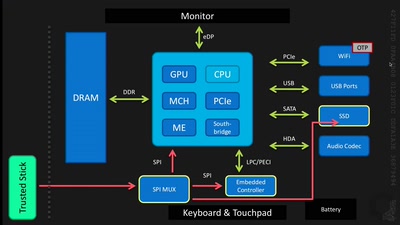
Extracting keys from FPGAs, OTP Tokens and Door Locks
Side-Channel (and other) Attacks in Practice

61 min
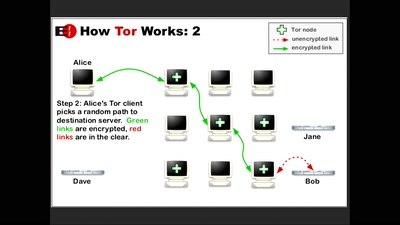
How Alice and Bob meet if they don't like onions
Survey of Network Anonymisation Techniques
60 min
Let's reverse engineer the Universe
exploring the dark

43 min
Sanitizing PCAPs
Fun and games until someone uses IPv6 or TCP

59 min
Hardsploit: A Metasploit-like tool for hardware hacking
A complete toolbox for IoT security

58 min
Taming the Chaos: Can we build systems that actually work?
Possible paths from today's ghastly hackery to what…

61 min
Code Pointer Integrity
... or how we battle the daemons of memory safety

58 min
Wie klimafreundlich ist Software?
Einblicke in die Forschung und Ausblick in die…

29 min
Der netzpolitische Wetterbericht
Wird es Regen geben? Ein Ausblick auf die neue…

61 min