Search for "24" returned 4347 results

61 min
Warum die Digitale Revolution des Lernens gescheitert ist.
Fünf Desillusionen

64 min
Source Code and Cross-Domain Authorship Attribution
The Role of Stylometry in Privacy

59 min
Memory Deduplication: The Curse that Keeps on Giving
A tale of 3 different memory deduplication based…

65 min
Von L2 auf EVPN-VXLAN in 4 Jahren
Migration eines PaaS-Netzwerks mit größtmöglichem…
54 min
"Day 2 Ops" Linux for Kubernetes and Container Workloads
Leveraging 10 years of Container Linux experience for…
48 min
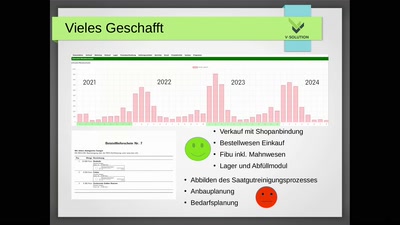
kivitendo - OpenSource ERP für den Saatgutanbau
Vom Acker - In die Welt

25 min
Regulating Autonomous Weapons
The time travelling android isn’t even our biggest problem

30 min
The ArduGuitar
An Arduino Powered Electric Guitar

43 min
Hirne Hacken
Menschliche Faktoren der IT-Sicherheit

53 min
When algorithms fail in our personal lives
Social media break up coordinator

62 min
Kyber and Post-Quantum Crypto
How does it work?

60 min
Concepts for global TSCM
getting out of surveillance state mode
91 min
What the World can learn from Hongkong
From Unanimity to Anonymity

26 min
Opening Event
35C3: Refreshing Memories
65 min
LatticeHacks
Fun with lattices in cryptography and cryptanalysis

39 min
ID Cards in China: Your Worst Nightmare
In China Your ID Card Knows Everything

49 min
Toward a Cognitive "Quantified Self"
Activity Recognition for the Mind

51 min
Uncovering vulnerabilities in Hoermann BiSecur
An AES encrypted radio system

51 min