Search for "28" returned 4265 results

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

61 min
Ten years after ‚We Lost The War‘
The future does not look much brighter than ten years ago.…

88 min
0, 1 oder 2
Hackerei und Cyberbrei
58 min
RFID Treehouse of Horror
Hacking City-Wide Access Control Systems

54 min
AMD x86 SMU firmware analysis
Do you care about Matroshka processors?
47 min
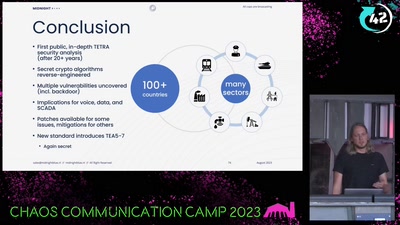
All cops are broadcasting
Obtaining the secret TETRA primitives after decades in the…

63 min