Search for "32" returned 4077 results
47 min
Hillbilly Tracking of Low Earth Orbit
Repurposing an Inmarsat Dish

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities
50 min
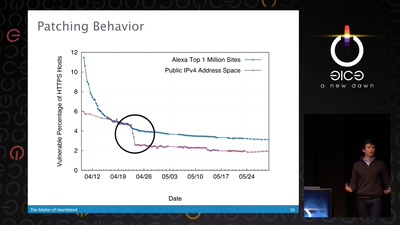
The Matter of Heartbleed
What went wrong, how the Internet reacted, what we can…
40 min
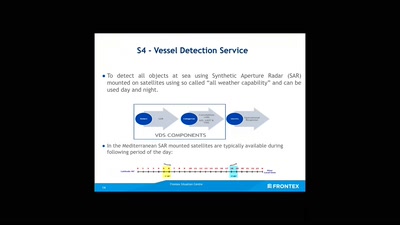
No roborders, no nation, or: smile for a European surveillance propagation
How an agency implements Fortress Europe by degrading…
38 min
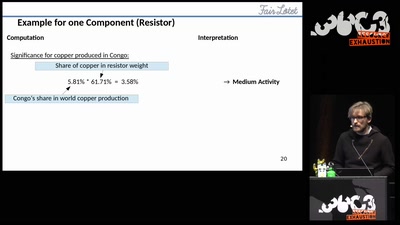
Fairtronics
A Tool for Analyzing the Fairness of Electronic Devices

36 min
Sim Gishel
A singing and dancing robot build to take part in casting…

30 min
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches

59 min
TamaGo - bare metal Go framework for ARM SoCs.
Reducing the attack surface with pure embedded Go.

40 min
Radical Digital Painting
Fantastic Media Manipulation
41 min
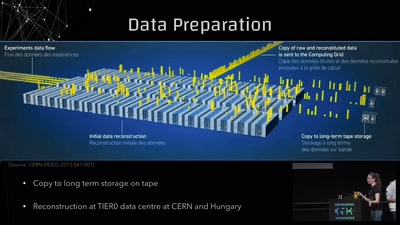
Conquering Large Numbers at the LHC
From 1 000 000 000 000 000 to 10: Breaking down 14 Orders…

57 min
Kryptographie nach Snowden
Was tun nach der mittelmäßigen Kryptographie-Apokalypse?

59 min
Hacking EU funding for a decentralizing FOSS project
Understanding and adapting EU legal guidelines from a FOSS…

62 min
radare demystified
after 1.0

60 min
The Only Thing We Know About Cyberspace Is That Its 640x480
One Terabyte of Kilobyte Age

60 min