Search for "windows" returned 684 results

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…

62 min
Bionic Ears
Introduction into State-of-the-Art Hearing Aid Technology
41 min
Infrastructure of a migratory bird
Technology and autonomy in more-than-human networks

37 min
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…
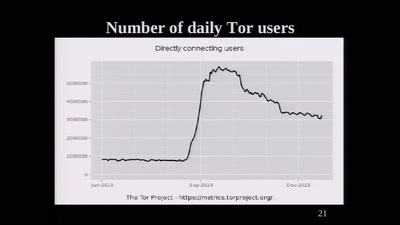
62 min
The Tor Network
We're living in interesting times

90 min
Security Nightmares
Damit Sie auch morgen schlecht von Ihrem Computer träumen.…

60 min
Intel Management Engine deep dive
Understanding the ME at the OS and hardware level

54 min
AMD x86 SMU firmware analysis
Do you care about Matroshka processors?

60 min
Dieselgate – A year later
env stinks || exit

30 min
The ArduGuitar
An Arduino Powered Electric Guitar

60 min
Why is GPG "damn near unusable"?
An overview of usable security research

32 min
History and implications of DRM
From tractors to Web standards

62 min
To Protect And Infect, Part 2
The militarization of the Internet

60 min
Check your privileges!
How to drop more of your privileges to reduce attack…

36 min