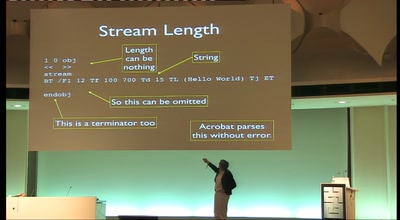
In this talk I demonstrate our research and the implementation of methods to detect cryptographic algorithms and their parameters in software. Based on
our observations on cryptographic code, I will point out several inherent characteristics to design signature-based and generic identification methods.